Author: Cybernoz
Citrix has disclosed two critical vulnerabilities affecting its NetScaler Console (formerly NetScaler ADM), NetScaler SVM, and NetScaler Agent, which could…
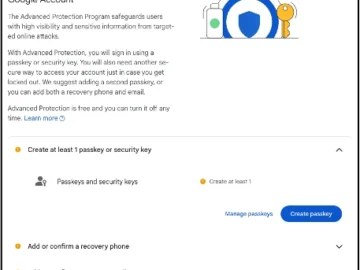
The password killers known as “passkeys” are now available to users of Google’s Advanced Protection Program, which works to add…
Google has removed a potential obstacle for high-risk users who want to enroll in the company’s Advanced Protection Program (APP):…
Jul 10, 2024NewsroomCybersecurity / Phishing Attack Google on Wednesday announced that it’s making available passkeys for high-risk users to enroll…
June 7, 2024 was the 70th anniversary of the death of Alan Turing, the father of modern computer science, whose…
Microsoft Patch Tuesday for July 2024 fixed 2 actively exploited zero-days Pierluigi Paganini July 10, 2024 Microsoft Patch Tuesday security…
A large-scale fraud campaign with over 700 domain names is likely targeting Russian-speaking users looking to purchase tickets for the…
Evolve Bank & Trust, a prominent financial services institution, has confirmed a data breach that has compromised the personal information…
Millions of Legal Documents Exposed Online! Sensitive data leak raises security concerns for the legal industry. Learn how this breach…
An investment company that had several proposals to build new datacentres in the south of England rejected by local planning…
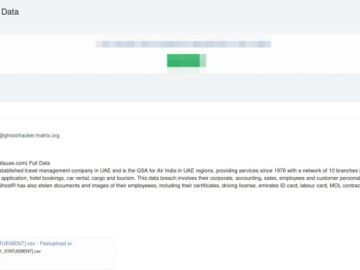
A threat actor known as “ghostr” on the XSS forum has claimed responsibility for a significant data breach targeting the…
A new flaw in OpenSSH can lead to remote code execution Pierluigi Paganini July 10, 2024 A vulnerability affects some…