Author: Cybernoz
Threat actors carry out man-in-the-middle attacks to intercept, tamper, and manipulate communications between two parties unknown to them. Consequently, they…
In collaboration with international partners, the U.S. Federal Bureau of Investigation (FBI) and the Cyber National Mission Force (CNMF) have…
Microsoft, the American technology giant, has issued an email request to all its employees in China to stop using Android…
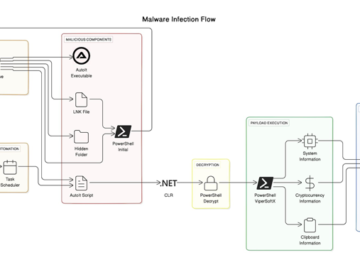
Jul 10, 2024NewsroomEndpoint Security / Threat Intelligence The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks…
Fujitsu, the renowned Japanese tech giant, has confirmed a data breach that compromised personal and business information of some individuals…
Morphisec researchers have discovered a critical zero-click remote code execution (RCE) vulnerability in Microsoft Outlook, designated CVE-2024-38021. Unlike the previously…
In today’s interconnected digital landscape, the threat posed by botnets continues to evolve, presenting significant challenges to corporate cybersecurity. Botnets,…
CISO HoneyBook | Israel | On-site – View job details As a CISO, you will develop and implement a multi-year…
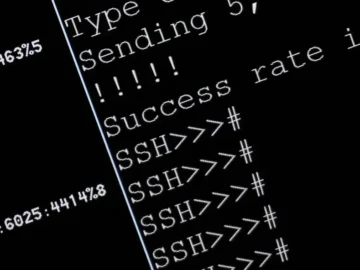
A new security vulnerability has been discovered within select versions of the OpenSSH secure networking suite, potentially exposing systems to…
Polyfill.io helps web developers achieve cross-browser compatibility by automatically managing necessary polyfills. By adding a script tag to their HTML,…
Technologies such as GenAI, ML and IoT are giving threat actors new tools that make it easier to target consumers…
In this Help Net Security interview, Jake King, Head of Threat & Security Intelligence at Elastic, discusses companies’ exposure to…