Author: Cybernoz
New variant of Mallox ransomware targets Linux systems using custom encryption and a builder web panel. Uptycs decryptor offers hope,…
Proton, the company behind Proton Mail, launched an end-to-end encrypted alternative to Google Docs, seeking to compete with the cloud…
A Technically Skilled individual who finds a bug faces an ethical decision: report the bug or profit from it. This…
Hackers stole OpenAI secrets in a 2023 security breach Pierluigi Paganini July 06, 2024 The New York Times revealed that…
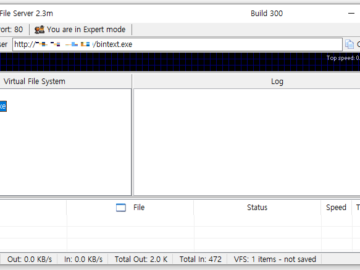
A proof-of-concept (PoC) exploit has been released for a critical remote code execution vulnerability in the HTTP File Server (HFS)…
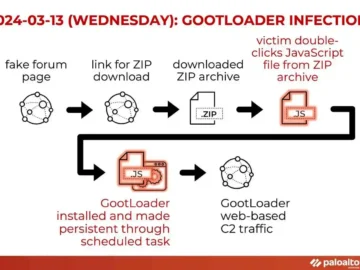
GootLoader, a sophisticated JavaScript-based malware has continued to challenge cybersecurity experts with its unique evasion techniques. However, researchers have discovered…
The cybercriminals who claimed responsibility for the Ticketmaster data breach say they’ve stolen 440,000 tickets for Taylor Swift’s Eras Tour….
Internet giant Cloudflare reports that its DNS resolver service, 1.1.1.1, was recently unreachable or degraded for some of its customers…
Malicious actors are targeting HTTP File Servers (HFS) from Rejetto by leveraging vulnerabilities to deploy malware and cryptocurrency mining software….
Hackers have leaked what they claim is Ticketmaster barcode data for 166,000 Taylor Swift Eras Tour tickets, warning that more…
Europol’s recent paper sheds light on formidable challenges posed by Privacy Enhancing Technologies (PET) in Home Routing systems. These technologies,…
Security breach potentially exposed internal secrets at AI research firm OpenAI after hackers accessed discussions on sensitive AI projects in…