Author: Cybernoz
A new DDoS botnet has emerged on the internet: the Zergeca botnet. This sophisticated threat, written in Golang, has garnered…
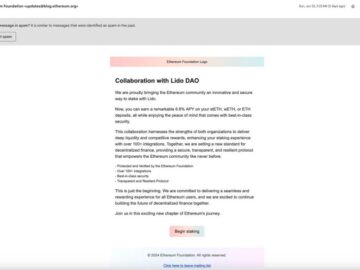
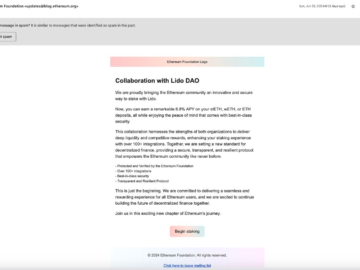
The Ethereum Foundation (EF) this week disclosed a phishing campaign that targeted its email subscribers. The attack that took place…
Hackers compromised Ethereum mailing list and launched a crypto draining attack Pierluigi Paganini July 05, 2024 Hackers compromised Ethereum ‘s…
Logsign, a web server built on Python for Unified Security Operations (SecOps), has successfully addressed critical vulnerabilities that could potentially…
Users of Twilio, the cloud-based communication service provider, are being alerted to a security breach affecting Authy, its platform for…
Software as a Service (SaaS) has revolutionized how businesses operate by offering convenient, scalable, and cost-effective solutions for various operational…
As the use of the cloud continues to be strategically vital to many organizations, cloud resources have become the biggest…
The BianLian ransomware group has allegedly launched a series of cyberattacks against three prominent US companies, compromising substantial volumes of…
Over the past six months, there has been a notable surge in Android financial threats – malware targeting victims’ mobile…
Jul 05, 2024NewsroomSupply Chain Attack / Malware The supply chain attack targeting widely-used Polyfill[.]io JavaScript library is wider in scope…
The explosion of Internet of Things (IoT) devices has brought about a wide range of security and privacy challenges, according…
Jul 05, 2024NewsroomNetwork Security / Cyber Attack Cybersecurity researchers have uncovered a new botnet called Zergeca that’s capable of conducting…







![Polyfill[.]io Attack Impacts Over 380,000 Hosts, Including Major Companies Polyfill Attack](https://image.cybernoz.com/wp-content/uploads/2024/07/Polyfillio-Attack-Impacts-Over-380000-Hosts-Including-Major-Companies-360x270.png)

