Author: Cybernoz
Twilio has confirmed that an unsecured API endpoint allowed threat actors to verify the phone numbers of millions of Authy…
Most accomplished cybercriminals go out of their way to separate their real names from their hacker handles. But among certain…
Ransomware has become a growing threat in our new hybrid world. It encrypts a victim’s files, rendering them inaccessible, and…
The United Nations Development Programme (UNDP) is pleased to announce a new partnership with the DFINITY Foundation, which will leverage…
In a disturbing evolution of ransomware tactics, a new group known as Volcano Demon has emerged, diverging from the usual…
HealthEquity Inc., the largest health savings account administrators in the U.S., has encountered a cybersecurity setback, as detailed in its…
FIA (Fédération Internationale de l’Automobile), the auto racing governing body since the 1950s, says attackers gained access to personal data…
Hackers are actively exploiting a remote code execution vulnerability in the HTTP File Server (HFS) program. The vulnerability, identified as…
ASUS and NordVPN partner for 1st routers with built-in VPN! Enhance your home network security & privacy with this innovative…
Europol coordinated a joint law enforcement action known as Operation Morpheus, which led to the takedown of almost 600 Cobalt…
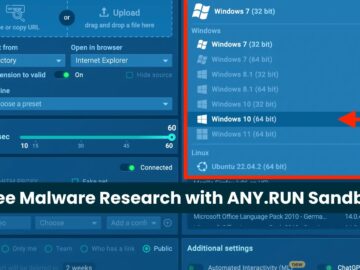
In a significant move to enhance cybersecurity analysis for all its users, ANY.RUN has announced that Windows 10 is now…
Hiap Seng Industries, a prominent engineering and construction company, has fallen victim to a ransomware attack that compromised its servers….