Author: Cybernoz
Gogs is a standard open-source code hosting system used by many developers. Several Gogs vulnerabilities have been discovered recently by…
Two vulnerabilities in Rockwell Automation PanelView Plus have been discovered. Unauthenticated attackers could exploit them remotely to perform remote code…
TotalEnergies Clientes SAU has reported a significant cyberattack that has compromised the personal data of 210,715 customers. The incident has…
Croatia’s biggest hospital, Zagreb Univ. Hospital Centre, was crippled by ransomware attack. LockBit 3.0 forced shutdown and data breach. Patients…
03 Jul Yahoo Still Ranks As The Largest Data Breach In History Posted at 09:05h in Blogs by Di Freeze…
Cyber Essentials was launched in the UK to much fanfare in June 2014, aiming to help businesses “to guard against…
In response to recent security vulnerabilities discovered in flagship Samsung models, the UAE Cyber Security Council has issued a critical…
Opaxe Pty Ltd, an Australian software and information services company for mining and minerals industry, has allegedly suffered a cyberattack….
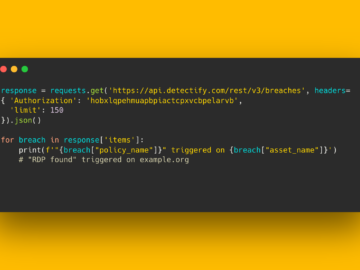
All Surface Monitoring users can configure Attack Surface Policies directly from the new Domains page, enabling various combinations of characteristics…
Hackers abuse phishing attacks as they are highly effective and low-cost methods for deceiving users into revealing sensitive information. Despite…
A vulnerability in Junos OS on SRX Series devices allows attackers to trigger a DoS attack by sending crafted valid…
Jul 03, 2024The Hacker NewsOSINT / Artificial Intelligence Recently the Office of the Director of National Intelligence (ODNI) unveiled a…