Author: Cybernoz
In recent weeks, security researchers have observed a surge in attacks exploiting Oracle Database Scheduler’s External Jobs feature to gain…
A teenage boy suspected of involvement in the Scattered Spider cyber attacks on two major Las Vegas casino operators, Caesars…
A cyberattack targeting a third-party technology vendor has disrupted passenger flights at major international airports across Europe, including Heathrow Airport…
A new method and proof-of-concept tool called EDR-Freeze demonstrates that evading security solutions is possible from user mode with Microsoft’s…
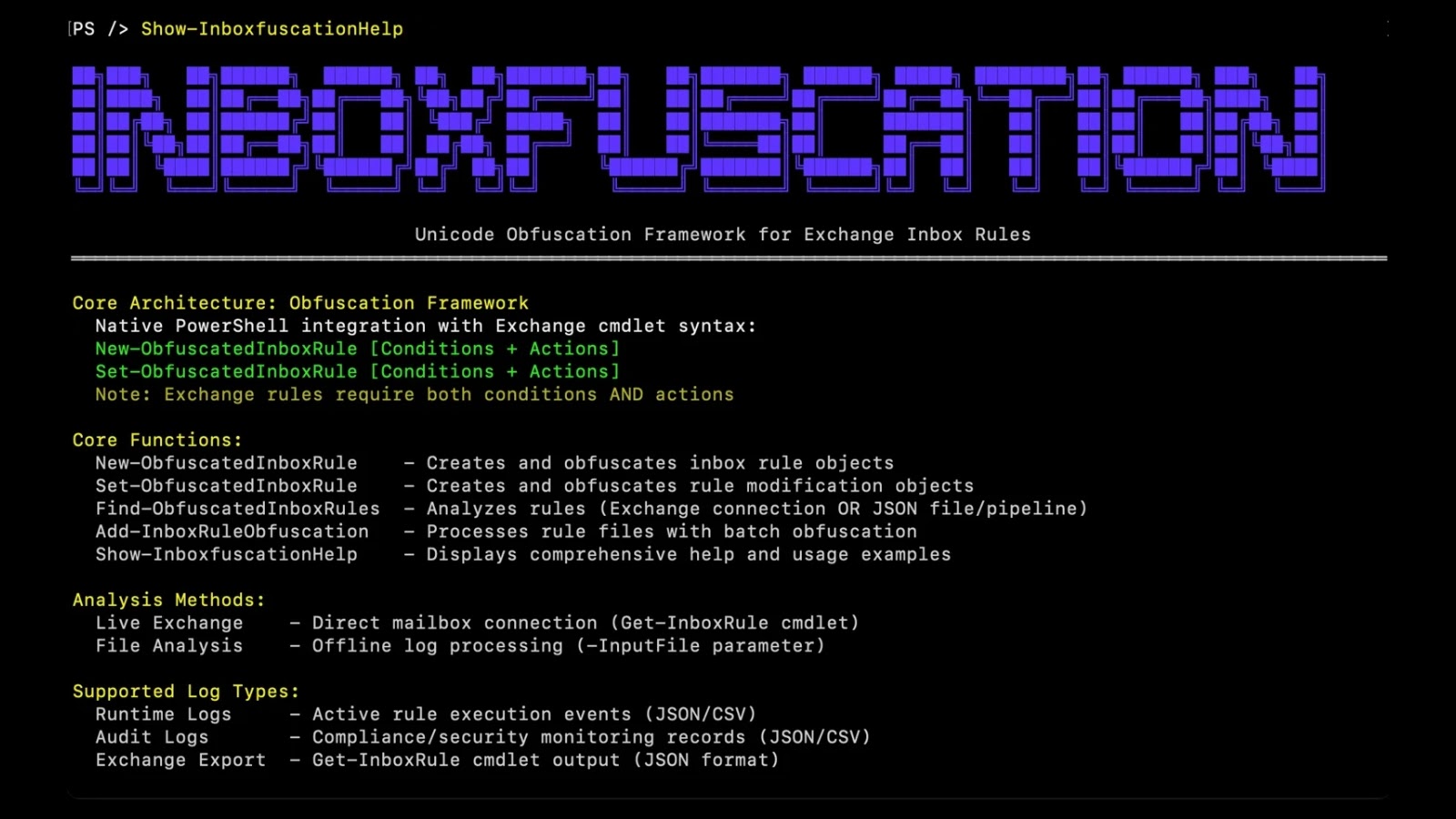
Attackers increasingly exploit Microsoft Exchange inbox rules to maintain persistence and exfiltrate data within enterprise environments. A newly released tool,…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. WASHINGTON — Cybersecurity…
LastPass is warning users of a campaign that targets macOS users with malicious software impersonating popular products delivered through fraudulent…
A sophisticated Iran-nexus espionage group known as Subtle Snail has emerged as a significant threat to European telecommunications, aerospace, and…
Not long ago, the mere idea that cryptocurrencies could ever be integrated into mainstream finance would have seemed like a…
Organizations in Belarus, Kazakhstan, and Russia have emerged as the target of a phishing campaign undertaken by a previously undocumented…
The recent wave of social engineering attacks highlights the risks of how a sophisticated threat group can take advantage of…
Mozilla has announced a new feature that enables Firefox extension developers to roll back to previously approved versions, allowing them…