Author: Cybernoz
Staff retention is currently a huge issue for companies across all industries, but nowhere more so than in the tech…
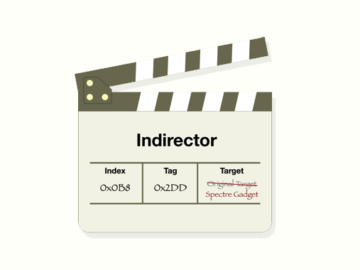
Researchers from the University of California have unveiled a novel high-precision Branch Target Injection (BTI) attack, dubbed “Indirector,” that exploits…
Google has unveiled kvmCTF, a new vulnerability reward program (VRP) explicitly targeting the Kernel-based Virtual Machine (KVM) hypervisor. This initiative,…
Today’s digital, on-demand age sees many organisations rely heavily on multiple cloud services for the day-to-day running of their operations….
In 2022, over 24 million passwords were exposed. Are passwords becoming pointless? Even if you have one, it seems like…
By the time the Senate unanimously confirmed Nate Fick to be America’s cyber ambassador in September 2022, tech diplomacy headaches…
Hackers often mimic penetration testing services to disguise their malicious activities as legitimate security assessments. By imitating authorized security testing,…
Jul 02, 2024NewsroomHardware Security / Vulnerability Modern CPUs from Intel, including Raptor Lake and Alder Lake, have been found vulnerable…
The Florida Department of Health, the first accredited public health system in the United States, has reportedly fallen victim to…
Something needs to change with cyber security. One study found that between 2021 and 2022, data breaches increased by over…
A new Orcinius Trojan has been discovered, employing VBA Stomping to hide its infection. The multi-stage trojan uses Dropbox and…
More than two-thirds (68%) of cyber-attacks are some outcome of human error or social engineering attack designed to target human frailties. As…