Author: Cybernoz
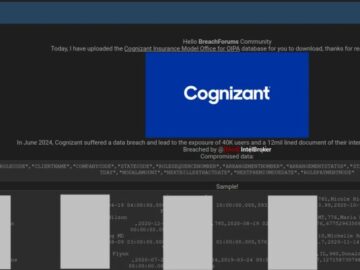
IntelBroker, a threat actor (TA) who is a prominent member of the notorious BreachForums, has allegedly leaked a trove of…
Prudential Financial data breach impacted over 2.5 million individuals Pierluigi Paganini July 02, 2024 Prudential Financial confirmed that more than…
Wise has warned some of its customers about a data breach at Evolve Bank & Trust, a bank they collaborated…
Transparent Tribe (aka APT36) has been active since 2016, focusing on social engineering strategies to target Indian government and military…
Nordic banks are turning more eagerly to artificial intelligence (AI) and innovation-led tech partnerships that can help them compete more…
Australian man charged for Evil Twin Wi-Fi attacks on domestic flights Pierluigi Paganini July 02, 2024 An Australian man has…
We challenge you to find us a business without an online presence. You’d have to go to a remote town…
Water Sigbin (8220 Gang) exploits vulnerabilities (CVE-2017-3506, CVE-2023-21839) in Oracle WebLogic servers to deliver cryptocurrency miners using PowerShell scripts. They…
NordVPN launches its third experimental product from the NordLabs platform. File Checker is an online tool that scans different types…
Artificial intelligence (AI) workloads are quite unlike those we’ve seen previously in the enterprise. And across the different phases of…
The nefarious LockBit 3.0 ransomware group has struck once again, targeting unsuspecting victims in their latest wave of attacks. The…
Wie, seriously, do you think the EU is taking cybersecurity? Let’s look at the numbers. As of 1 day ago,…