Author: Cybernoz
China-linked APT exploited Cisco NX-OS zero-day to deploy custom malware Pierluigi Paganini July 02, 2024 Cisco fixed an actively exploited…
Prudential Financial, a leading financial services company, has reported a data breach that has affected over 2.5 million individuals. The…
TeamViewer has confirmed that the cyberattack on its systems was orchestrated by Russian threat actors, specifically the APT29 or Midnight…
Jul 02, 2024NewsroomCyber Espionage / Vulnerability A China-nexus cyber espionage group named Velvet Ant has been observed exploiting a zero-day…
Thank you for joining! Access your Pro+ Content below. 2 July 2024 UKtech50 2024: The most influential people in UK…
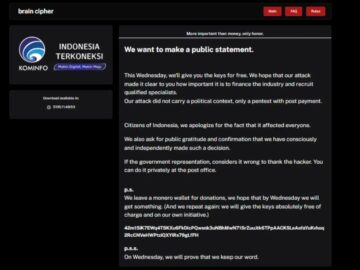
The notorious hacking group Brain Cipher has released decryption keys for free, allowing victims to recover their encrypted data without…
Jul 02, 2024NewsroomDigital Regulation / Tech News Meta’s decision to offer an ad-free subscription in the European Union (E.U.) has…
Affirm Holdings, a prominent U.S. financial technology firm, announced that the personal information of Affirm card users may have been…
Did a threat actor lie about orchestrating a data breach containing sensitive data about 8,000 students and faculty of a university…
Australia’s leading financial institutions are bracing for what could be the most significant cyber attack in the history of the…
In this Help Net Security interview, Lingping Gao, CEO at NetBrain, discusses the challenges NetOps teams face in maintaining production…
Jul 02, 2024NewsroomData Theft / Wi-Fi Security An Australian man has been charged with running a fake Wi-Fi access point…