Author: Cybernoz
Geisinger Healthcare, a leading provider in Pennsylvania’s healthcare sector, has recently disclosed a data breach involving the unauthorized access of…
Juniper Networks has disclosed a critical vulnerability (CVE-2024-2973) affecting its Session Smart Router (SSR) and Session Smart Conductor products. The…
Cyberespionage actors are increasingly using ransomware as a final attack stage for financial gain, disruption, or to cover their tracks,…
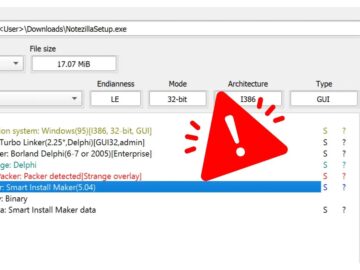
Cybersecurity firm Rapid7 has identified that popular Windows tools Notezilla, RecentX, and Copywhiz have been weaponized to deliver malware. These…
Geisinger Health System discovered a data breach involving the personal information of over one million patients. The breach was traced…
TeamViewer, a leading provider of remote access software, has announced a security breach in its corporate network due to an…
US announces a reward for Russia’s GRU hacker behind attacks on Ukraine Pierluigi Paganini June 28, 2024 The US DoJ…
Recently, commuters in California, Paris, Singapore, Queensland, and London have been encountering Apple Inc.’s Safari Browser ads on billboards and…
Jun 28, 2024NewsroomData Breach / Enterprise Security TeamViewer on Thursday disclosed it detected an “irregularity” in its internal corporate IT…
In recent years, the threat posed by state-sponsored ransomware actors has become increasingly pronounced, with malicious cyber activities orchestrated by…
In this Help Net Security interview, Michelle Weston, VP of Security & Resiliency at Kyndryl, discusses the key challenges in…
The Australian Football League (AFL) has made significant progress in protecting its digital identities and safeguarding sensitive information by leveraging…