Author: Cybernoz
Dafydd Stuttard | 27 June 2024 at 11:36 UTC We are excited to announce a strategic investment from Brighton Park…
Threat actors use RATs because they provide attackers with persistent access to compromised systems, enabling long-term espionage and exploitation. North…
It’s no secret that the Olympics is one of the most highly attended events in the world. This year, it…
The University Hospital Centre Zagreb (KBC Zagreb) is under cyberattack that started on Wednesday night, the Croatian Radiotelevision has reported….
Experts are raising eyebrows after OpenAI announced a one-month delay in the rollout of its highly anticipated “Voice Mode” feature…
The owners of Polyfill.io have relaunched the JavaScript CDN service on a new domain after polyfill.io was shut down as…
Malware storage, distribution, and command and control (C2) operations are increasingly being used to leverage cloud services for recent cybersecurity…
Partnership with BCR Cyber Will Provide Jobs and Access to Advanced Experiential Training at Maryland Community Colleges Baltimore, MD (6/25/24)…
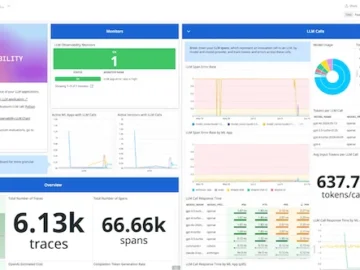
Datadog announced LLM Observability, which allows AI application developers and ML engineers to efficiently monitor, improve and secure large language…
Did you know it’s now possible to build blockchain applications, known also as decentralized applications (or “dApps” for short) in…
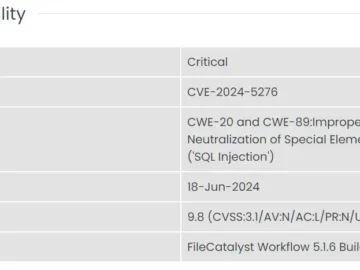
A critical security flaw has been reported in Fortra FileCatalyst Workflow, a widely used platform designed for efficient file exchange…
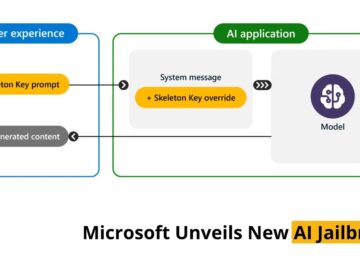
Hackers frequently look for new ways to bypass the ethical and safety measures incorporated into AI systems. This gives them…