Author: Cybernoz
A custom platform developed by SITU Research aided the International Criminal Court’s prosecution in a war crimes trial for the…
The Fortra FileCatalyst Workflow is vulnerable to an SQL injection vulnerability that could allow remote unauthenticated attackers to create rogue…
In a significant move to bolster data privacy protections, the California Privacy Protection Agency (CPPA) inked a new partnership with…
Microsoft has released the Windows 11 KB5039302 preview update for Windows 11 version 22H2, bringing several new features and fixes. Since…
Security researchers face significant challenges when hunting for vulnerabilities in Large Language Models (LLMs). However, Google’s Naptime Framework provides a…
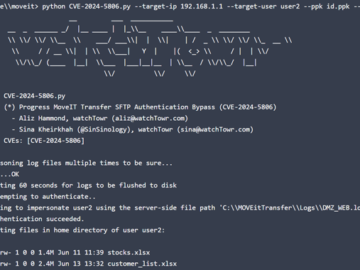
Jun 26, 2024NewsroomVulnerability / Data Protection A newly disclosed critical security flaw impacting Progress Software MOVEit Transfer is already seeing…
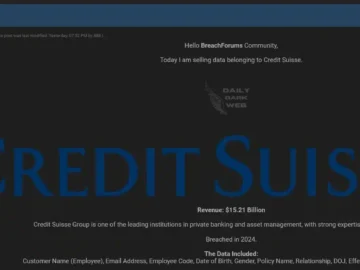
Credit Suisse, a global investment bank and financial services firm, has reportedly fallen victim to a cyberattack. The Credit Suisse…
Threat actors are already trying to exploit a critical authentication bypass flaw in Progress MOVEit Transfer, less than a day…
Polyfill.js is a JavaScript library that gives modern functionality on older browsers without native support for some web features. Polyfills…
A shockwave went through the financial world when ransomware group LockBit claimed to have breached the US Federal Reserve, the…
The June 2024 optional update for Windows 10 is now available. Today’s update brings KB5039299 for Windows 10 version 22H2 with up…
A new ELF malware tool named k4spreader, written in Cgo by the Chinese “8220” (Water Sigbin) mining gang, was discovered…