Author: Cybernoz
A novel Android attack vector from a piece of malware tracked as Snowblind is abusing a security feature to bypass…
Hackers abuse CHM files because they can embed malicious scripts or code within them. Windows systems often trust and execute…
Cybersecurity researchers have identified a new ransomware payload associated with the P2Pinfect malware, primarily targeting Redis servers. This sophisticated malware,…
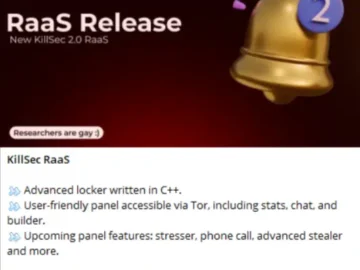
Hacktivist group KillSec has revealed a new weapon in their digital arsenal: a Ransomware as a Service (RaaS) program designed…
Hackers attack AI infrastructure platforms since these systems contain a multitude of valuable data, algorithms that are sophisticated in nature,…
By Mike Fleck, Head of Product Marketing at DigiCert Digital trust is at the core of what makes internet connected…
26 Jun 2024 Cybersecurity Almanac: 100 Facts, Figures, Predictions And Statistics Posted at 08:52h in Blogs by Di Freeze This…
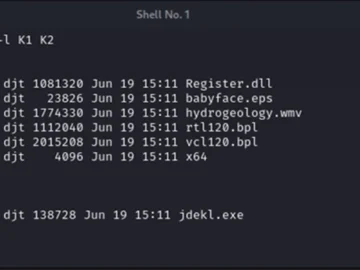
A newly spotted campaign is leveraging BPL sideloading and other uncommon tricks to deliver the IDAT Loader (aka HijackLoader) malware…
Jun 26, 2024NewsroomFirmware Security / Vulnerability Apple has released a firmware update for AirPods that could allow a malicious actor…
Notorious ransomware group BianLian has claimed to have added two new organizations as its latest cyberattack victims. The BianLian ransomware…
Microsoft addressed a Remote code execution vulnerability on their Bluetooth service on March 2023 Patch Tuesday. This vulnerability could allow…
OilRig is an Iranian-linked cyber espionage group that has been active since 2015, and this group is known for its…