Author: Cybernoz
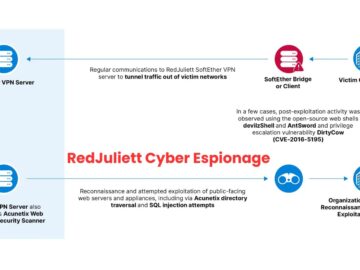
A suspected Chinese state-sponsored cyberespionage group, RedJuliett, targeted the Taiwanese government and academic, technological, and diplomatic organizations between November 2023…
A new threat actor has emerged, claiming a zero-day vulnerability in the Linux GRUB bootloader that allows for local privilege…
24 Jun 5 Of The Highest-Paying Cybersecurity Jobs Right Now Posted at 08:53h in Blogs by Di Freeze This week…
Buckinghamshire Council has deployed Copilot for Microsoft 365 to improve operational efficiency. By using Microsoft’s artificial intelligence (AI) tool, the…
Levi Strauss & Co., a renowned American clothing company, has disclosed a significant data breach affecting over 72,000 customers. The…
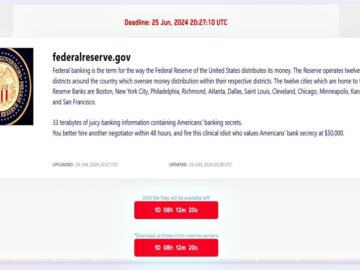
The notorious LockBit ransomware gang claims to have breached the Federal Reserve Board (Federalreserve.gov), the central banking system of the…
Pure Storage makes a big deal of its subscription models of purchasing for storage hardware. It believes it can offer…
Researchers at SonarCloud have discovered critical security vulnerabilities in Mailcow, a popular open-source email server solution, that could have allowed…
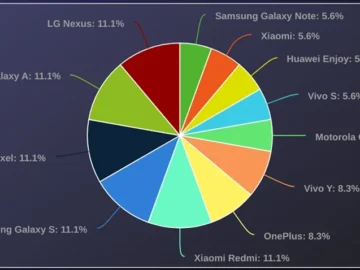
The open-source Rafel RAT is being leveraged by multiple threat actors to compromise Android devices and, in some cases, to…
Jun 24, 2024The Hacker NewsThreat Intelligence / Cybersecurity Learn about critical threats that can impact your organization and the bad…
The Sellafield nuclear waste site has pleaded guilty to criminal charges brought by the industry regulator, admitting to significant cyber…
Yana Li, Director of IT & Platform Security at WebBeds, embodies resilience, determination, and a passion for cybersecurity that has…