Author: Cybernoz
22 Jun Demand For Better Cybersecurity Fuels A Booming Job Market Posted at 08:55h in Blogs by Di Freeze This…
Jun 22, 2024NewsroomCyber Espionage / Threat Intelligence Russian organizations have been targeted by a cybercrime gang called ExCobalt using a…
The rolling series of breaches targeting customers of cloud platform Snowflake appears to be a supply chain attack wrapped in…
Experts found a bug in the Linux version of RansomHub ransomware Pierluigi Paganini June 22, 2024 The RansomHub ransomware operators…
Jun 22, 2024NewsroomNational Security / Cyber Espionage The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) imposed…
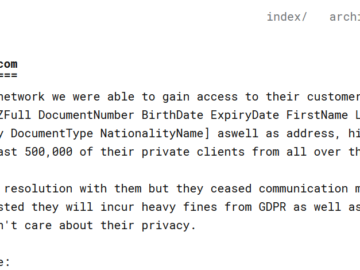
The Los Angeles Unified School District (LAUSD) has fallen victim to a significant data breach. A hacker identified as “Satanic”…
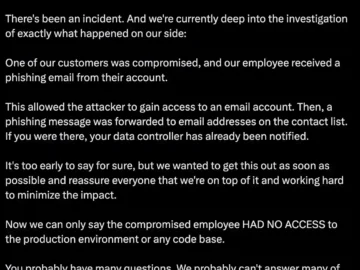
ANY.RUN has disclosed a recent cybersecurity incident in which one of its employees fell victim to a sophisticated phishing attack,…
The UK’s Sellafield nuclear waste site has pleaded guilty to criminal charges related to various cybersecurity failings in the period…
The Los Angeles Unified School District has confirmed a data breach after threat actors stole student and employee data by…
A day after the Biden administration announced a U.S. ban on the sale of Kaspersky Lab products, the U.S. Treasury…
The Treasury Department’s Office of Foreign Assets Control (OFAC) has sanctioned twelve Kaspersky Lab executives for operating in the technology sector…
“They’d only get in trouble if they summarized the story incorrectly and made it defamatory when it wasn’t before. That’s…