Author: Cybernoz
Threat actors are actively exploiting a SolarWinds Serv-U path-traversal vulnerability, leveraging publicly available proof-of-concept (PoC) exploits. Although the attacks do…
In a concerning development for cybersecurity, hackers are increasingly leveraging Progressive Web Apps (PWAs) to execute sophisticated phishing attacks aimed…
Have you ever heard of a Doctrine meant to formulate cyber space operations? Well, here’s a news piece that might…
Jun 20, 2024NewsroomCyber Espionage / Hacking News State-sponsored actors with ties to Russia have been linked to targeted cyber attacks…
Researchers have discovered that various threat actors groups associated with Chinese state-linked espionage have been conducting a sustained hacking campaign…
China-linked spies target Asian Telcos since at least 2021 Pierluigi Paganini June 20, 2024 A China-linked cyber espionage group has…
Car dealership SaaS platform CDK Global suffered an additional breach Wednesday night as it was starting to restore systems shut…
1inch, a leading DeFi aggregator that provides advanced security solutions to users worldwide, has announced today the launch of the…
1inch, a leading DeFi aggregator that provides advanced security solutions to users across the entire space, has announced today the…
Hunting for Volt Typhoon, a sophisticated and stealthy cyber threat actor with unknown malware components “living off the land”, is…
Jun 20, 2024NewsroomFirmware Security / Vulnerability Cybersecurity researchers have disclosed details of a now-patched security flaw in Phoenix SecureCore UEFI…
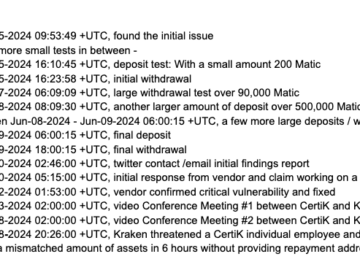
In a high-stakes clash within the crypto verse, Kraken, a leading U.S. cryptocurrency exchange, has accused blockchain security firm Certik…