Author: Cybernoz
Stuxnet, a complex worm discovered in 2010, targeted Supervisory Control and Data Acquisition (SCADA) systems used in industrial facilities. By…
Outside-In Approach to Partners Key to Firm’s Continued Growth Welcome to the new SonicWall! 2024 marks a high note in…
We caught up with Pure Storage CEO Charlie Giancarlo at the company’s Accelerate event in Las Vegas this week. He…
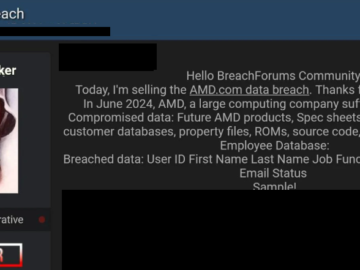
Chip maker giant AMD investigates a data breach Pierluigi Paganini June 19, 2024 AMD announced an investigation after a threat…
“We’ve now got a huge industry of AI-related companies who are incentivized to do shady things to continue their business,”…
Cybersecurity researchers have uncovered a sophisticated malware campaign orchestrated by a threat actor group, Void Arachne. This group has targeted…
By Elaina Farnsworth, Co-founder & CEO — SkillFusion The surging popularity of electric vehicles (EVs) is marking a strong push…
As our reliance on technology continues to grow, so does the sophistication and prevalence of cyber threats. And with each…
19 Jun Cybercrime Surges As Security Spending Falls Short In Thailand Posted at 09:03h in Blogs by Di Freeze This…
Pure Storage will upgrade its Fusion control plane to make storage capacity across its arrays available via storage classes that…
Hackers often abuse weaponized Word docs, as they can contain macros that contain or exploit flaws inside those Word files…
Hackers are offering “free” mobile data access on Telegram channels by exploiting loopholes in telecom provider policies, which target users…