Author: Cybernoz
Cybersecurity firm Sygnia has discovered a sophisticated cyberespionage campaign allegedly linked to China. Their research shared with Hackread.com ahead of…
Independent forensic accountants contracted to investigate controversial Post Office Horizon system in 2012 describe Post Office cover-ups, threats, obstruction and…
ANZ Plus customers will be able to reuse their banking identity with certain merchants and businesses via the ConnectID service….
Fake websites of authoritative and popular companies claiming to be genuine sites make users believe that the site belongs to…
An Irish hacker, who was involved in cyberattacks at the age of 13, has now walked free from court after…
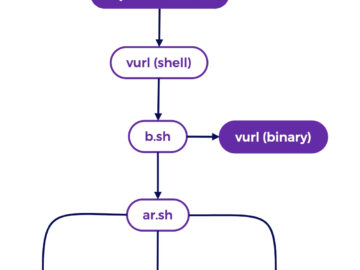
Cryptojacking campaign targets exposed Docker APIs Pierluigi Paganini June 19, 2024 A malware campaign targets publicly exposed Docker API endpoints…
Managing cybersecurity for any organization is no easy feat. Improving cybersecurity maturity is often even more difficult, made increasingly challenging…
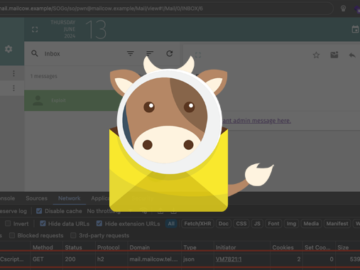
Jun 19, 2024NewsroomEmail Security / Vulnerability Two security vulnerabilities have been disclosed in the Mailcow open-source mail server suite that…
The FBI’s Baltimore Field Office is actively seeking to identify potential victims of Richard Michael Roe, who has recently been…
Trellix has patched a critical security vulnerability in its Intrusion Prevention System (IPS) Manager, CVE-2024-5671. This flaw, caused by insecure…
The Federal Trade Commission (FTC) has launched legal action against software giant Adobe and two of its top executives, Maninder…
Google Chrome users worldwide are being warned about a targeted cyber attack specifically aimed at Android browsers across various devices….