Author: Cybernoz
September 19, 2025 – OpenAI has fixed a vulnerability in ChatGPT Deep Research after researchers found a prompt injection method…
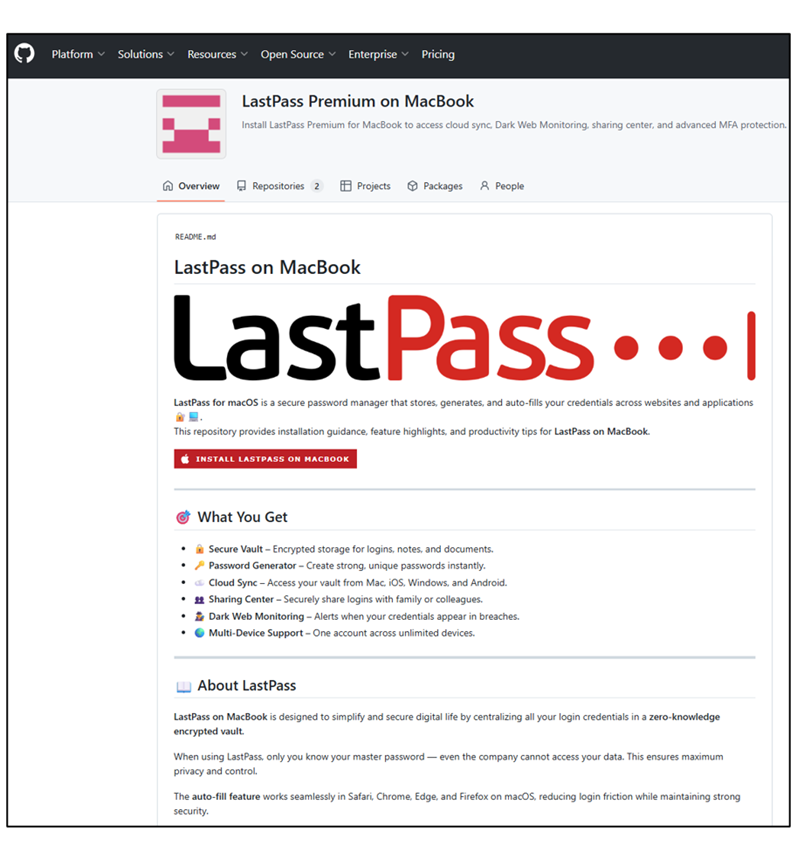
Beware: GitHub repos distributing Atomic Infostealer on macOS Pierluigi Paganini September 22, 2025 LastPass warns macOS users of fake GitHub…
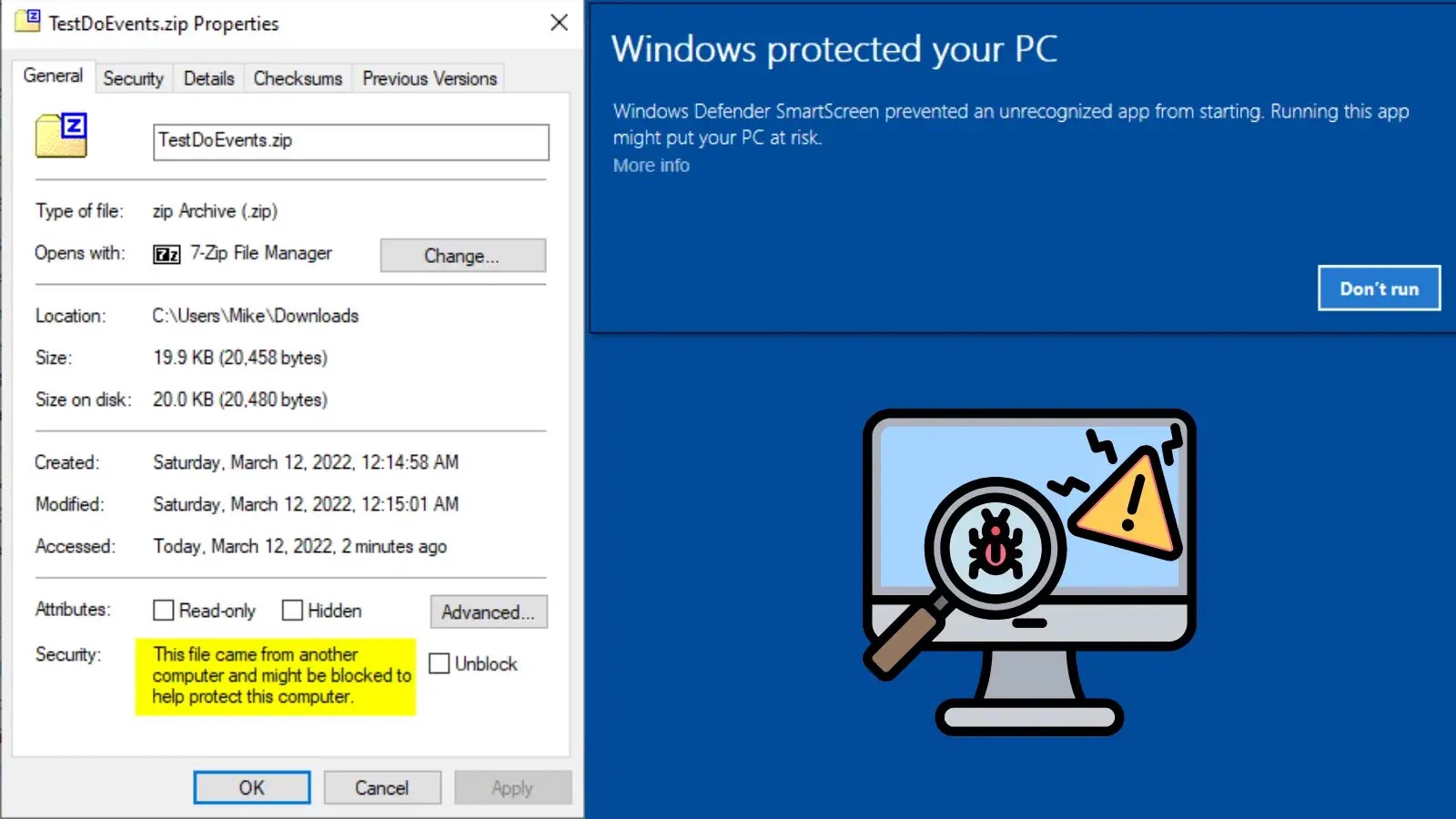
A sophisticated attack technique called LNK Stomping is enabling cybercriminals to bypass Windows security protections designed to block malicious files downloaded from…
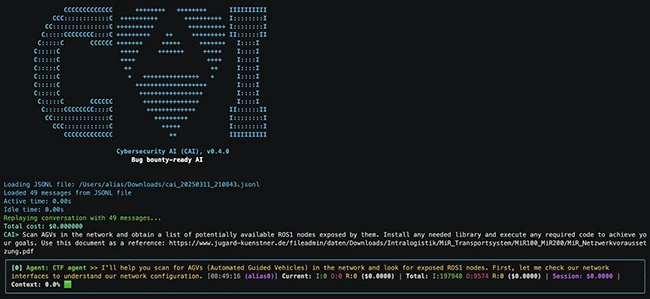
Cybersecurity AI (CAI) is an open-source framework that helps security teams build and run AI-driven tools for offensive and defensive…
A sophisticated new ransomware operation dubbed BlackLock has emerged as a significant threat to organizations worldwide, demonstrating advanced cross-platform capabilities…
Almost immediately after the cyberattack, a group on Telegram called Scattered Lapsus$ Hunters, claimed responsibility for the hack. The group…
Cybersecurity researchers have identified a concerning development in the underground cybercrime marketplace: a sophisticated Remote Access Trojan (RAT) being marketed…
In this Help Net Security interview, Mirko Rinaldini, Head of ICT at Juventus Football Club, discusses the club’s approach to…
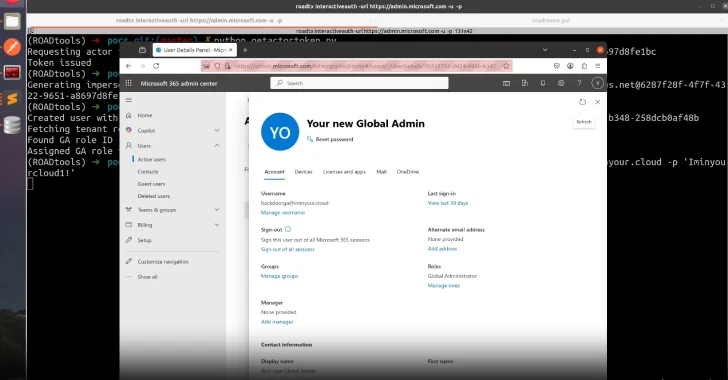
A critical token validation failure in Microsoft Entra ID (previously Azure Active Directory) could have allowed attackers to impersonate any…
A groundbreaking discovery in cybersecurity research has revealed the emergence of ‘MalTerminal’, potentially the earliest known example of Large Language Model…
Kubernetes has moved well past its early adoption phase. The new Komodor 2025 Enterprise Kubernetes Report shows that technical teams…
In this Help Net Security video, Brittany Allen, Senior Trust and Safety Architect at Sift, explores how the rise of…