Author: Cybernoz
The Monetary Authority of Singapore (MAS) has announced a new requirement impacting all major retail banks in the country to…
Unraveling Human Factors in Data Breaches Data spillage is a term used to describe the exposure of sensitive or classified…
Cyble Research & Intelligence Labs (CRIL) analyzed 21 vulnerabilities in its weekly vulnerability report for the second week of July,…
The Central Bureau of Investigation (CBI) of India has uncovered a large-scale human trafficking operation that has ensnared thousands of…
Amidst the recent conflict, the Israeli army’s vital operational cloud computing systems became the target of an extensive wave of…
The weekly cyber security newsletter is a brief summary of what the most recent threats, vulnerabilities, and innovations in the digital security…
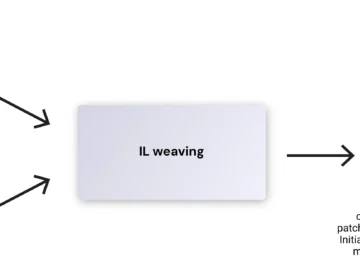
A sophisticated malware campaign targeting the NuGet package manager has been uncovered by researchers. The ongoing attack, which began in…
Rite Aid Corporation, a prominent American drugstore chain headquartered in Philadelphia, has fallen victim to a data breach following a…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Hackers stole call, text records…
When a potential threat emerges, organizations must act quickly. Yet despite this urgency, response times often lag, leaving systems vulnerable…
Indonesia has achieved a new milestone in restoring 86 public services following the Temporary National Data Center cyberattack. The cyberattack…
Artificial Intelligence (AI) has revolutionized numerous fields, including cybersecurity. However, its application in cyber-crime represents a dual-edge sword, offering both…