Author: Cybernoz
Excelsior Orthopaedics, a leading musculoskeletal healthcare center in New York, has been allegedly targeted by the notorious MONTI ransomware group….
A critical security vulnerability has been discovered in HCL Domino, a popular enterprise server software, that could potentially expose sensitive…
Frankfurt University of Applied Sciences announced on Monday that it had fallen victim to a cyberattack, leading to a complete…
The Europol Platform for Experts (EPE) has allegedly faced a data breach incident, resulting in the leakage of sensitive data….
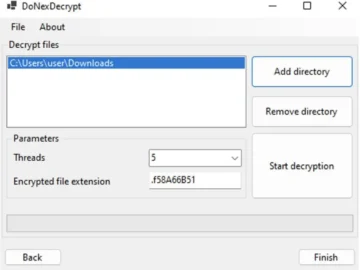
Researchers discovered a flaw in the DoNex ransomware’s encryption scheme, allowing them to create a decryptor for DoNex and its…
Jul 09, 2024NewsroomSupply Chain Attack / Web Security Unknown threat actors have been found propagating trojanized versions of jQuery on…
The notorious Rhysida ransomware group has added MYC Media to its long list of high-profile victims. MYC Media is a…
Australian investigations into the breach of two organisations in 2022 form the basis of an international advisory on APT40, a…
Symantec, a cybersecurity firm based in California, has issued a warning to all 1.5 billion Apple device users regarding a…
Microsoft is suffering cybersecurity failures due to systemic problems with strategic leadership. The world is witnessing an alarming trend of…
In this Help Net Security interview, Koma Gandy, VP of Leadership and Business at Skillsoft, addresses the critical aspects of…
Researchers have discovered a critical flaw in the cryptographic schema of the DoNex ransomware and all of its variants and…