Author: Cybernoz
A critical security vulnerability in MongoDB Compass, identified as CVE-2024-6376, has been discovered, potentially exposing systems to code injection attacks….
The day is slowly turning into night, and the American special operators are growing concerned. They are deployed to a…
The Egyptian Health Department (EHD) has reported a data breach affecting 121,995 individuals, including one resident of Maine. The breach,…
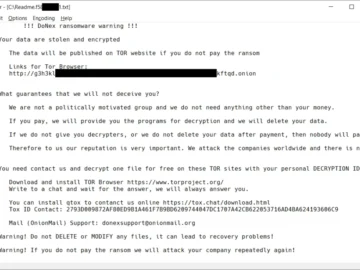
A cryptographic weakness in the DoNex ransomware and its previous incarnations – Muse, fake LockBit 3.0, and DarkRace – has…
On a popular hacking form, a user has leaked a file that contains 9,948,575,739 unique plaintext passwords. The list appears…
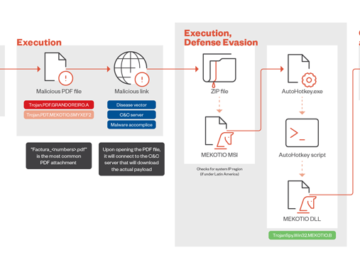
Jul 08, 2024NewsroomMalware / Cyber Threat Financial institutions in Latin America are being threatened by a banking trojan called Mekotio…
Generative AI (GenAI) is rapidly becoming an integral part of our lives and a powerful force for driving value within…
An alarming new threat has emerged targeting cybersecurity researchers. An archive containing malicious code is being distributed on the social…
A new position paper argues that Privacy Enhancing Technologies (PET) used in Home Routing are making it difficult for law…
By Ian Thornton-Trump, CISO, Cyjax “There are three ways to make a living in this business: be first, be smarter,…
Hackers attack Microsoft SmartScreen as it’s a cloud-based, anti-phishing, and anti-malware component that determines whether a website is potentially malicious,…
Jul 08, 2024NewsroomVulnerability / Software Security Four unpatched security flaws, including three critical ones, have been disclosed in the Gogs…