Author: Cybernoz
The task of managing and interpreting vast amounts of data is akin to finding a needle in a haystack. Cyber…
A leading cybersecurity company has become the latest victim of a sophisticated phishing attack. The incident, which began in late…
United States prosecutors have secured a deal with WikiLeaks founder Julian Assange requiring the long-embattled publisher to plead guilty to…
A new method of distributing the Remcos Remote Access Trojan (RAT) has been identified. This malware, known for providing attackers…
25 Jun The Best Cybersecurity Bootcamps Of 2024 Posted at 08:53h in Blogs by Di Freeze This week in cybersecurity…
While almost three-quarters (74%) of in-progress SAP S/4HANA implementation projects are being deployed on public clouds, analyst Gartner has urged…
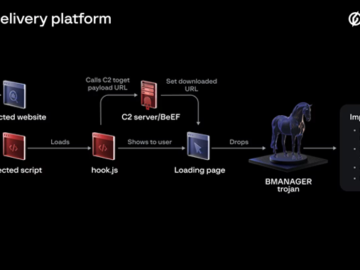
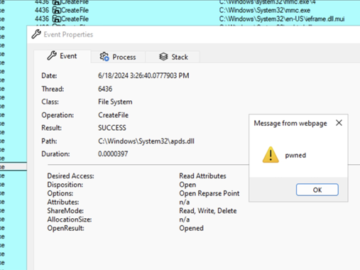
Jun 25, 2024NewsroomData Theft / Web Security A previously undocumented threat actor dubbed Boolka has been observed compromising websites with…
WikiLeaks founder Julian Assange has walked free from prison and will no longer be extradited from the UK, after reaching…
Cyber hygiene encompasses all practices and steps taken to prevent your accounts and devices from becoming vulnerable to cyber threats….
Attackers are leveraging a new infection technique called GrimResource that exploits MSC files. By crafting malicious MSC files, they can…
Ransomware attackers wielding a LockBit variant dubbed Brain Cipher have disrupted a temporary national data center facility which supports the…
Jun 25, 2024NewsroomVulnerability / Threat Detection Threat actors are exploiting a novel attack technique in the wild that leverages specially…