Author: Cybernoz
Researchers at Graz University of Technology were able to spy on users’ online activities simply by monitoring fluctuations in the…
Thank you for joining! Access your Pro+ Content below. 25 June 2024 A revolution in space Share this item with…
P2PInfect, originally a dormant peer-to-peer malware botnet with unclear motives, has finally come alive to deploy a ransomware module and…
Wordfence Threat Intelligence team identified a significant security breach involving multiple WordPress plugins. The initial discovery was made when the…
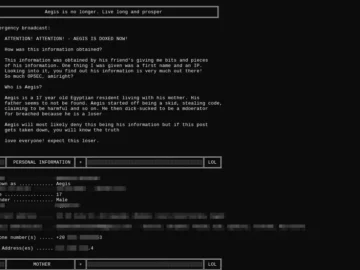
The infamous cybercrime marketplace BreachForums faced an awkward scenario on June 25, 2024, when a threat actor leaked unverified information…
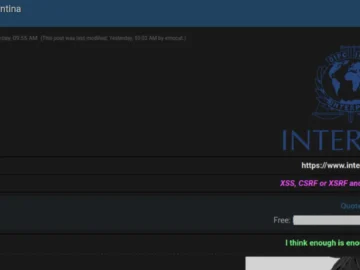
The National Central Bureau (NCB) Buenos Aires, a vital division of Interpol in Argentina, has been listed by a dark…
Windows IIS Servers often host critical web applications and services that provide a gateway to sensitive data and systems due…
WikiLeaks founder Julian Assange has been released from prison after reaching a deal with the U.S. government. The agreement, announced…
A new supply chain attack has impacted several plugins hosted on WordPress.org. This WordPress vulnerability, discovered on June 24th, 2024,…
NAB has rapidly scaled up the number of engineers working with Amazon’s AI coding assistant from 450 to 1000 within…
CISA confirmed that its CSAT environment was breached in January. Pierluigi Paganini June 25, 2024 CISA warned chemical facilities that…
A Zip Slip vulnerability was discovered in Artifactory, the leading software repository manager, allowing attackers to execute arbitrary code through…