Author: Cybernoz
“Panamorfi,” a new DDoS attack, exploits Discord, Minecraft, and Jupyter Notebooks. Cybersecurity researchers warn of this threat targeting misconfigured Jupyter…
The Federal Bureau of Investigation (FBI) issued a public service announcement warning the public about scammers impersonating cryptocurrency exchange employees…
Aug 02, 2024Ravie LakshmananCyber Espionage / Malware A Taiwanese government-affiliated research institute that specializes in computing and associated technologies was…
Privacy-focused search engine DuckDuckGo has been blocked in Indonesia by its government after citizens reportedly complained about pornographic and online…
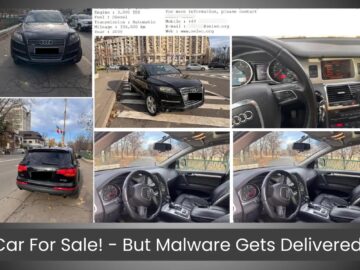
A Russian threat actor known as Fighting Ursa (also referred to as APT28, Fancy Bear, and Sofacy) has been identified…
In recent reports, our Cybersecurity Insiders have detailed how hackers have been generating revenue through cyberattacks such as ransomware. However,…
Researchers from ANY RUN identified a malware distribution campaign dubbed DeerStealer that leverages deceptive websites masquerading as legitimate Google Authenticator…
Avtech camera vulnerability actively exploited in the wild, CISA warns Pierluigi Paganini August 02, 2024 CISA warned that an Avtech…
Cybersecurity company CrowdStrike has been sued by investors who say it provided false claims about its Falcon platform after a bad security…
A sophisticated phishing campaign targets Microsoft OneDrive users, employing social engineering to trick victims into executing malicious PowerShell scripts. The…
A recent study revealed that employees typically download around 30GB of data monthly from SaaS applications to their devices, including…
Critically, in today’s world, cyber security is a fundamental part of statecraft and the responsibility of the government. That being…