Author: Cybernoz
In a move to responsibly incorporating artificial intelligence (AI) into cybersecurity, the Cybersecurity and Infrastructure Security Agency (CISA) has announced…
Damian Williams, the United States Attorney for the Southern District of New York, announced that Vinoth Ponmaran has been sentenced…
Today, the National Crime Agency (NCA) revealed the successful shutdown of Russian Coms, a sophisticated fraud platform responsible for defrauding…
As artificial intelligence (AI) continues to advance, its impact on cybersecurity becomes increasingly profound. AI-generated cyber attacks are evolving rapidly,…
40% of tested environments allowed attack paths that lead to domain admin access, according to Picus Security. Achieving domain admin…
In the rapidly evolving world of cybersecurity, staying ahead of emerging threats and leveraging cutting-edge technologies is paramount. Vimal Mani,…
A dark web actor has taken responsibility for a data breach involving ADT, the American security firm renowned for its…
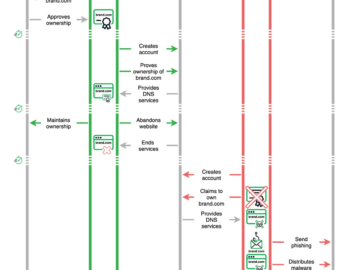
Sitting Ducks attack technique exposes over a million domains to hijacking Pierluigi Paganini August 02, 2024 Researchers warn of an…
Twenty-four prisoners were freed today in an international prisoner swap between Russia and Western countries. Among the eight Russians repatriated…
Twenty-four prisoners were freed today in an international prisoner swap between Russia and Western countries. Among the eight Russians repatriated…
The National Crime Agency is analysing huge quantities of data seized from an online platform to identify hundreds of criminals…
Researchers have uncovered a cyber espionage campaign targeting a Taiwanese government-affiliated research institute specializing in computing and related technologies. The…