Author: Cybernoz
Recently, many Android phone users may have received emails about the activation and use of the ‘Find My Device’ feature….
Jun 19, 2024NewsroomZero-Day Exploits / Cyber Espionage The China-nexus cyber espionage actor linked to the zero-day exploitation of security flaws…
The Kraken crypto exchange disclosed today that alleged security researchers exploited a zero-day website bug to steal $3 million in…
Amtrak notified its customers regarding a significant security breach involving its Amtrak Guest Rewards accounts. The breach between May 15,…
Cybersecurity as a Service Market By Aashi Mishra, Content Writer, Research Nester The increased internet usage, all across the globe,…
A recent security advisory from Broadcom, now the owner company of VMware, discloses critical vulnerabilities affecting VMware vCenter Server and…
Small and Medium Size Enterprises (SMEs) are a major driver of the U.S. economy, representing as much as one-third of…
Key elections are being held in the UK, the US, the EU, and India, with many other countries also set…
Threat actor IntelBroker, notorious for a series of daring cyberattacks, has resurfaced with claims of orchestrating a data breach of…
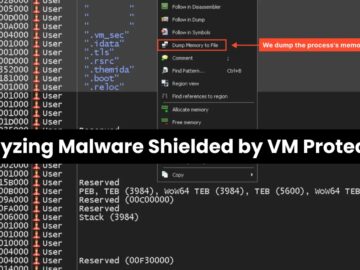
Researchers analyzed six malware families that are using the protectors Themida and VMProtect. None of the samples used code virtualization,…
Stuxnet, a complex worm discovered in 2010, targeted Supervisory Control and Data Acquisition (SCADA) systems used in industrial facilities. By…
Outside-In Approach to Partners Key to Firm’s Continued Growth Welcome to the new SonicWall! 2024 marks a high note in…