Author: Cybernoz
VMware fixed RCE and privilege escalation bugs in vCenter Server Pierluigi Paganini June 18, 2024 VMware addressed vCenter Server vulnerabilities…
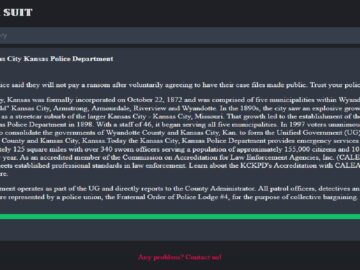
The Kansas City, Kansas Police Department (KCKPD) is facing a major security breach after the notorious BlackSuit ransomware group leaked…
Jun 18, 2024NewsroomPrivacy / Encryption A controversial proposal put forth by the European Union to scan users’ private messages for…
Internet Computer Protocol (ICP), a decentralized blockchain network that extends the functionality of Web3 by overcoming the limitations of traditional…
An independent fund, imec.xpand, is benefiting from a partnership with Belgian research giant imec to find the right investments and…
The Federal Trade Commission has filed a complaint in US federal court against Adobe and two executives, Maninder Sawhney and…
The Department of Public Health (DPH) under the County of Los Angeles has been involved in a significant data breach…
Atsign introduces NoPorts to offer a secure remote access solution, exceeding current limitations and setting a new standard for secure…
Two suspected administrators of a $430 million dark web marketplace are facing the possibility of life sentences in the United…
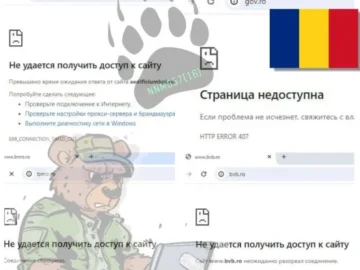
Several pro-Russia hacker groups have allegedly carried out a massive Distributed Denial-of-Service (DDoS) attack in Romania on June 18, 2024….
Two men have pleaded guilty to hacking into a federal law enforcement database to steal personal information of those they…
By Kenneth Moras Introduction: In today’s interconnected business environment, reliance on innovative vendors and open source solutions is inevitable. However,…