Author: Cybernoz
A 22-year-old British national allegedly linked to the Scattered Spider hacking group and responsible for attacks on 45 U.S. companies…
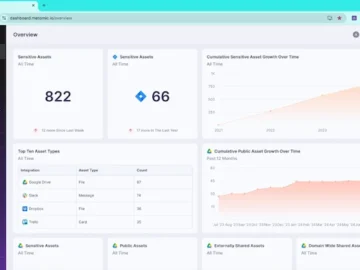
Metomic launched its new integration with Google Groups. The feature enables IT and security teams to ensure data loss prevention…
This week on TCE Cyberwatch, we report on significant breaches affecting both prominent companies and universities, with thousands of individuals…
LA County’s Department of Public Health (DPH) data breach impacted over 200,000 individuals Pierluigi Paganini June 17, 2024 The County…
A ransomware cyber attack targeted Synnovis, a pathology laboratory that processes blood tests for several NHS organizations, primarily in southeast…
17 Jun Help Wanted: Women In Cybersecurity Posted at 08:55h in Blogs by Di Freeze This week in cybersecurity from…
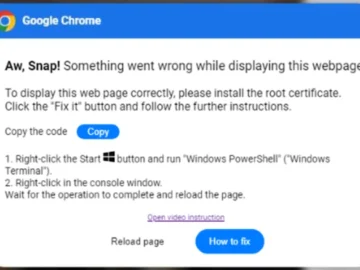
Attackers are increasingly using a clever social engineering technique to get users to install malware, Proofpoint researchers are warning. The…
By Milica D. Djekic The progress distribution is a slow and time-consuming process that normally might take decades and sometimes…
Jun 17, 2024NewsroomCyber Espionage / Vulnerability A suspected China-nexus cyber espionage actor has been attributed as behind a prolonged attack…
Traditional incident response (IR) processes, honed for on-premises environments, face significant challenges when applied to the cloud. The shared responsibility…
Cybersecurity researcher Jeremiah Fowler discovered a non-password-protected database containing 474,651 images belonging to Total Fitness, a health club chain with…
A Pakistani threat actor group, Cosmic Leopard, has been conducting a multi-year cyber espionage campaign named Operation Celestial Force, targeting…