Author: Cybernoz
Borrer Executive Search, an AESC-accredited boutique search and selection firm headquartered in Lausanne, Switzerland, has allegedly fallen victim to the…
Jun 14, 2024NewsroomArtificial Intelligence / Data Protection Microsoft on Thursday revealed that it’s delaying the rollout of the controversial artificial…
Trends in online fraud detection often act as the canary in the coal mine when it comes to understanding and…
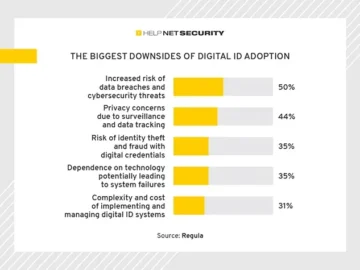
As innovative digital verification methods continue to emerge, the debate around their reliability and effectiveness is heating up, according to…
Microsoft has announced that it will delay the broad release of its AI-powered Recall feature for Windows Copilot+ PCs, following…
Here’s a look at the most interesting products from the past week, featuring releases from Acronis, Diligent, Entrust, KELA, Plainsea,…
Microsoft is delaying the release of its AI-powered Windows Recall feature to test and secure it further before releasing it…
HackerOne provides security capabilities for AWS customers looking to improve security in their cloud applications. These include vulnerability pentests specific…
Leading U.S. commercial bank Truist confirmed its systems were breached in an October 2023 cyberattack after a threat actor posted…
A significant data breach has exposed the private information of more than 1,200 Baw Baw Shire residents who contacted customer…
Securing Organizational Buy-in For Ethical Hackers CISOs and other security leaders are challenged to demonstrate the benefits of working with…
IMAGE: MIDJOURNEY Ascension, one of the largest U.S. healthcare systems, revealed that a May 2024 ransomware attack was caused by…