Author: Cybernoz
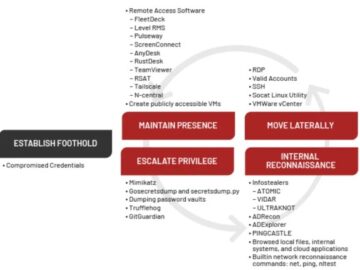
The financially motivated UNC3944 threat group has shifted focus to data theft extortion from software-as-a-service applications but without the use…
The Toronto District School Board is investigating a recent ransomware attack that affected its testing environment. The Toronto board is…
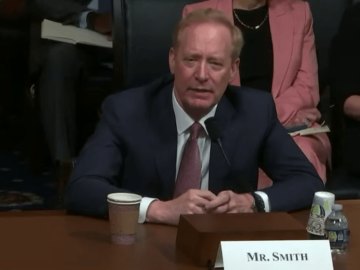
Microsoft president Brad Smith has testified before a US House panel on homeland security, fielding questions about its security practices…
The New York Times notified an undisclosed number of contributors that some of their sensitive personal information was stolen and…
Microsoft’s cybersecurity efforts have been roundly criticized in recent months, and despite pledges to do better, the company has compounded…
The Department of Health and Aged Care is piloting a new platform to streamline staff hire and management in the…
U.S. food chain giant Panera Bread is notifying employees of a data breach after unknown threat actors stole their sensitive personal…
The Toronto District School Board (TDSB) is warning that it suffered a ransomware attack on its software testing environment and…
Numerous government-operated websites have fallen victim to a cyber attack resembling a distributed denial of service (DDoS) assault. In this…
Update June 13, 13:01 EDT: GrapheneOS says CVE-2024-32896 is the same as CVE-2024-29748. Google added a new CVE ID to track the…
The way we work has drastically changed over the last few years. Our data, users, devices, and applications are now…
A proof-of-concept (PoC) exploit for a critical Veeam Recovery Orchestrator authentication bypass vulnerability tracked as CVE-2024-29855 has been released, elevating the…