Author: Cybernoz
The ‘cybersecurity poverty line’ was a term coined over ten years ago by a Cisco security leader, Wendy Nather. We…
The potential of artificial intelligence (AI) to help companies measure and optimise their sustainability efforts could be outweighed by the…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert about a recent impersonation scam in which scammers…
Cybersecurity firm Resecurity has uncovered the latest campaign from the notorious cybercriminal group Smishing Triad targeting smartphone users in Pakistan….
Traceable AI just released a report on the escalating concerns surrounding API security within the financial services sector. The comprehensive…
The Labour Party manifesto for the 2024 general election has promised to support the tech and digital sectors through a…
Please see below comments by Kevin Surace, Chair, Token & “Father of the Virtual Assistant” for your consideration regarding ant…
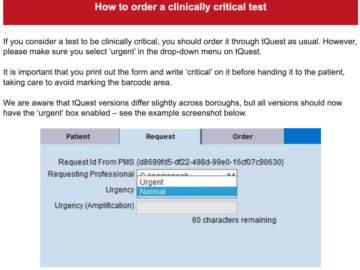
In the aftermath of the Synnovis ransomware attack that struck last week, London hospitals continue to struggle to deliver patient…
Jun 13, 2024NewsroomThreat Intelligence / Mobile Security The threat actor known as Arid Viper has been attributed to a mobile…
A vulnerability in the Microsoft Windows Error Reporting Service, which was identified and patched three months ago in the March…
YouTube reportedly now injects ads directly into video streams to make it more difficult for ad blockers to block advertisements….
WARMCOOKIE is a new Windows backdoor that is deployed by a phishing effort with a recruiting theme dubbed REF6127. The…