Author: Cybernoz
Artificial intelligence (AI) companies cannot be relied on to voluntarily share information about system capabilities and risk, say current and…
AI SPERA, a leader in Cyber Threat Intelligence (CTI) solutions, announced that it has started selling its paid threat detection…
Today, people around the world will head to school, doctor’s appointments, and pharmacies, only to be told, “Sorry, our computer…
VPN apps for Android increase privacy and security over the internet since connection data is encrypted, consequently making it impossible…
10 Jun Watch The New 90-Second National Cybersecurity Alliance Video Posted at 09:51h in Blogs by Di Freeze This week…
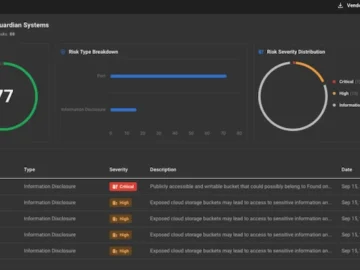
KELA launched the Third-Party Risk Management (TPRM) module, fully integrated into its threat intelligence platform. This new offering is specifically…
Google has revealed that it took down 1,320 YouTube channels and 1,177 Blogger blogs as part of a coordinated influence…
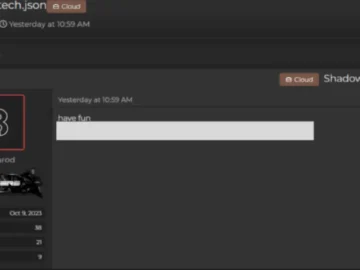
A dark web actor named “komarod” is claiming credit for a June 8 Shadow PC data breach, allegedly stealing data…
Apple is set to make a significant announcement at the Worldwide Developers Conference (WWDC), which kicks off on June 10. According to Bloomberg’s Mark Gurman, the tech giant will introduce…
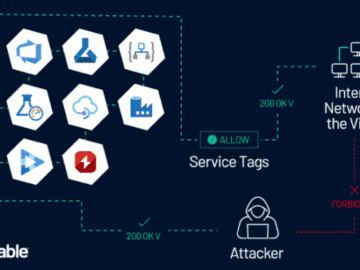
Jun 10, 2024NewsroomCloud Security / Vulnerability Microsoft is warning about the potential abuse of Azure Service Tags by malicious actors…
SAP talked a lot about artificial intelligence (AI) and generative AI at its annual Sapphire customer event in Orlando last…
By Joe Guerra, M.Ed, CASP+, Professor of Cybersecurity, Hallmark University When we talk about the cloud, it’s not just a…