Author: Cybernoz
SolarWinds has fixed a high-severity vulnerability (CVE-2024-28995) affecting its Serv-U managed file transfer (MFT) server solution, which could be exploited…
Google announced that it will reduce the amount of personal data it is storing by automatically deleting old data from…
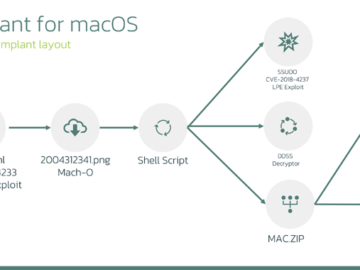
Cybersecurity researchers have disclosed that the LightSpy spyware allegedly targeting Apple iOS users is in fact a previously undocumented macOS…
Threat prevention, detection and incident response specialist Bitdefender is to make its managed detection and response (MDR) service free to…
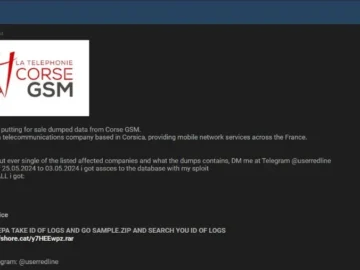
A major French telecommunications company, Corse GSM, has allegedly been hit by a massive data breach. It could have a…
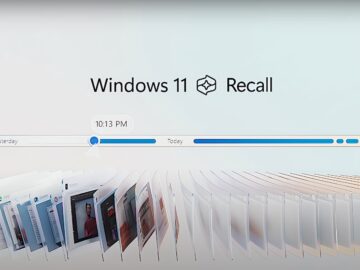
Following massive customer pushback after it announced the new AI-powered Recall for Copilot+ PCs last month, Microsoft says it will…
When Microsoft named its new Windows feature Recall, the company intended the word to refer to a kind of perfect,…
Following a brief hiatus after law enforcement agencies, including Europol and the FBI, disrupted their activities, the LockBit ransomware group…
Jun 07, 2024The Hacker NewsCyber Hygiene / Webinar 2023 was a year of unprecedented cyberattacks. Ransomware crippled businesses, DDoS attacks…
British tech entrepreneur and founder of Autonomy, Mike Lynch, has been acquitted of all charges, following a 12-week trial in…
The Computer Emergency Response Team of Ukraine (CERT-UA) reports about a new campaign dubbed “SickSync,” launched by the UAC-0020 (Vermin)…
Amid the ongoing elections for the European Parliament, the Russia-aligned NoName057(16) cyber criminal operation says it is launching extensive distributed…