Author: Cybernoz
Cybersecurity researchers have discovered a new malware loader codenamed CountLoader that has been put to use by Russian ransomware gangs…
October 2, 2025, marks the end of general support for VMware’s version 7. After that, Broadcom won’t release any new…
The Python Software Foundation team has invalidated all PyPI tokens stolen in the GhostAction supply chain attack in early September,…
A critical vulnerability in Microsoft’s Entra ID could have allowed an attacker to gain complete administrative control over any tenant…
After countless attacks across a multitude of organizations, the cyber security industry has a fairly good grasp of how adversaries…
SquareX first discovered and disclosed Last Mile Reassembly attacks at DEF CON 32 last year, warning the security community of…
Palo Alto, California, September 18th, 2025, CyberNewsWire SquareX first discovered and disclosed Last Mile Reassembly attacks at DEF CON 32…
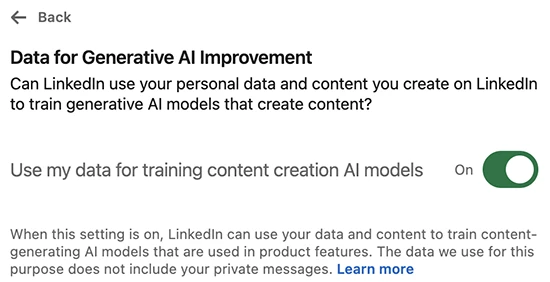
LinkedIn is making major changes to its User Agreement and Privacy Policy, effective November 3, 2025. Among the most notable…
AI’s growing role in enterprise environments has heightened the urgency for Chief Information Security Officers (CISOs) to drive effective AI…
Two men, named as Owen Flowers and Thalha Jubair, have today appeared before Westminster Magistrate’s Court in connection with a…
APT28, the long-running actor tracked as Fancy Bear, Sofacy and Sednit, used a compact but technically sophisticated campaign that researchers…
Emerging in mid-2025, the shinysp1d3r ransomware-as-a-service (RaaS) platform represents the next evolution of cloud-focused extortion tools. Unlike traditional ransomware that…