Author: Cybernoz
Live Nation, the parent company of Ticketmaster, has confirmed “unauthorized activity” on its database after hackers claimed to have stolen…
The Spanish National Police have successfully dismantled a large-scale illegal IPTV service, TVMucho (also known as Teeveeing), which had amassed…
Jun 03, 2024NewsroomMalware / Cyber Attack The North Korea-linked threat actor known as Andariel has been observed using a new…
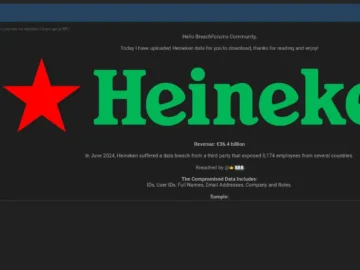
Dark web actor 888 on BreachForums has alleged a Heineken data breach. The cyber intrusion, according to the threat actor’s…
A critical security vulnerability has been discovered in the wpDataTables – WordPress Data Table, Dynamic Tables & Table Charts Plugin,…
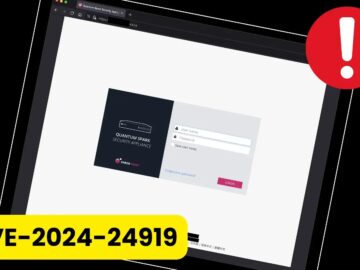
A critical zero-day vulnerability, CVE-2024-24919, has been discovered in Check Point Security Gateways, enabling the IPSec VPN or Mobile Access…
June 1, 2024 – Live Nation has confirmed what everyone has been speculating on for the last week: Ticketmaster has…
The University of Hyderabad (UoH), a prominent academic institution in India, finds itself entangled in a cybersecurity challenge as a…
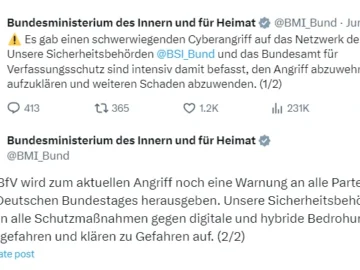
Germany’s Christian Democratic Union (CDU) found itself the target of a cyber assault over the weekend. The large-scale CDU cyberattack…
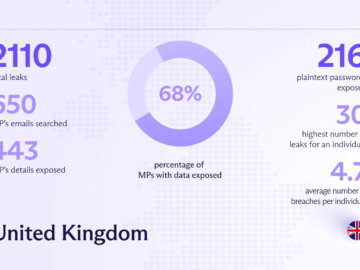
Experts found information of European politicians on dark web Pierluigi Paganini June 03, 2024 Personal information of hundreds of British…
Kaspersky has recently introduced a new free tool that is specifically built to thoroughly scan Linux operating systems for any…
Threat actors have claimed responsibility for a data breach involving Heineken employees. The news broke through a post on the…