Author: Cybernoz
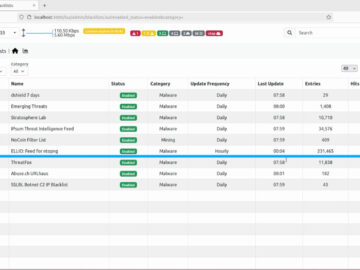
ELLIO, a provider of real-time, highly accurate intelligence for filtering of unwanted network traffic and cybernoise, and ntop, a provider…
31 May Learn How To Go Passwordless In 60 Seconds Posted at 09:00h in Blogs by Di Freeze This week…
Personal information of current and former BBC employees has been exposed in a data breach that affected the broadcaster’s in-house…
The operators of RedTail cryptominer, which was the biggest cryptominer operation last year, have now started to take advantage of…
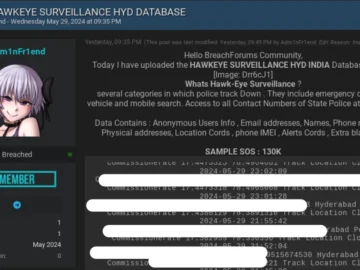
Hawk Eye, a popular citizen-friendly crime reporting app of Telangana State Police in India, appears to have been hit by…
A new variant of AllaKore RAT, named AllaSenha, has been discovered targeting Brazilian bank accounts, which leverages a multi-stage infection…
Hackers target IT industries as they hold valuable data, possess critical infrastructure, and often have access to sensitive information from…
Why Zero Access Is a Better Way To Protect Your Backup Infrastructure By Greg Tevis, Vice President of Strategy, Cobalt…
May 31, 2024NewsroomThreat Detection / Endpoint Security Digital content is a double-edged sword, providing vast benefits while simultaneously posing significant…
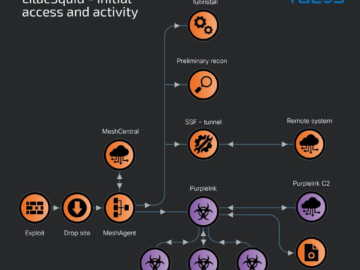
LilacSquid APT targeted organizations in the U.S., Europe, and Asia since at least 2021 Pierluigi Paganini May 31, 2024 A…
In recent cyberattacks, hackers are actively exploiting stored cross-site scripting (XSS) vulnerabilities in various WordPress plugins. According to Fastly reports,…
A data leak incident involving Clarity.fm left the personal data of business leaders and celebrities exposed to public access. Learn…