Author: Cybernoz
Google has released an emergency security update for its Chrome web browser to address a high-severity zero-day vulnerability that is…
During his 30-minute keynote speech Dong addressed key issues, including Taiwan, the South China Sea and China’s take on regional…
In this podcast, we ask Patrick Smith, EMEA chief technology officer at Pure Storage, about the increased drive towards ensuring…
Heightened risk related to data sovereignty is universally acknowledged. Most IT decision makers see that risk increasing as a result…
Cyber incidents linked to third-party systems used by the NSW government have more than quadrupled over the past two years,…
The Chinese state-sponsored threat actor TA415 has evolved its tactics, techniques, and procedures by leveraging legitimate cloud services like Google…
The ShinyHunters extortion group claims to have stolen over 1.5 billion Salesforce records from 760 companies using compromised Salesloft Drift OAuth…
Since early 2025, cybersecurity teams have observed a marked resurgence in operations attributed to MuddyWater, an Iranian state–sponsored advanced persistent…
The Jaguar Land Rover cyberattack that has shuttered production lines since September 1 will extend for at least another week,…
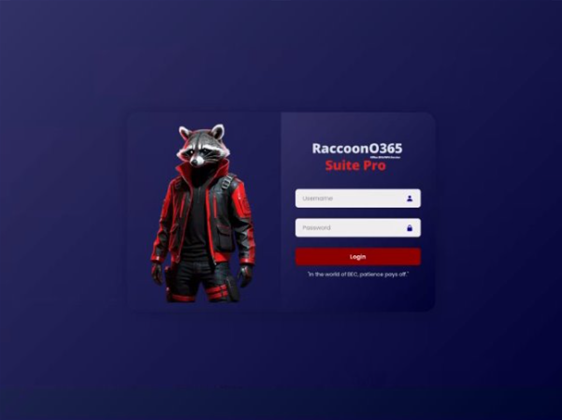
The Digital Crimes Unit (DCU) at Microsoft said it has disrupted a global phishing operation called RaccoonO365, uncloaking the leader…
China-linked APT41 targets government, think tanks, and academics tied to US-China trade and policy Pierluigi Paganini September 17, 2025 China-linked…
SonicWall said it confirmed an attack on its MySonicWall.com platform that exposed customers’ firewall configuration files — the latest in…