Author: Cybernoz
In today’s digital age, where technology is deeply ingrained in our daily lives, ensuring the cybersecurity of our educational institutions…
The first instance of Redline using such a method is in a new variant of Redline Stealer malware that McAfee…
IBM’s latest quarterly earnings filing coincided with the company’s plans to spend $6.4bn acquiring HashiCorp. IBM reported revenue of $14.5bn,…
UnitedHealth confirms that Change Healthcare’s network was breached by the BlackCat ransomware gang, who used stolen credentials to log into the company’s…
Today, Keeper Security joins Williams Racing as an Official Partner on the eve of the F1 Miami Grand Prix. Trusted…
The Biden administration is updating the US government’s blueprint for protecting the country’s most important infrastructure from hackers, terrorists, and…
After blocking 100% of “in-the-wild” malware samples that were deployed in multiple, consecutive third-party tests conducted by the AVLab Cybersecurity…
Apr 30, 2024NewsroomDocker Hub / Supply Chain Attack Cybersecurity researchers have discovered multiple campaigns targeting Docker Hub by planting millions…
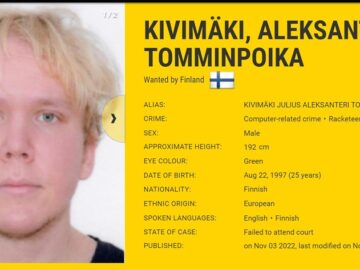
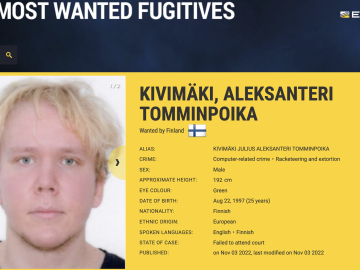
Julius Kivimäki, one of Europe’s most sought-after cyber criminals, has been sentenced to more than six years jail for attempting…
Synopsys has unveiled Polaris Assist, an innovative AI-powered application security assistant incorporated into the Synopsys Polaris Software Integrity Platform®. Leveraging…
A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into…
Researchers have uncovered a novel infection chain associated with the DarkGate malware. This Remote Access Trojan (RAT), developed using Borland…