Author: Cybernoz
Researchers have uncovered a novel infection chain associated with the DarkGate malware. This Remote Access Trojan (RAT), developed using Borland…
The future of the Internet and new innovations, such as the metaverse and Web 3.0, is at a crossroads. The…
There are proof-of-concept techniques allowing attackers to achieve persistence on Palo Alto Networks firewalls after CVE-2024-3400 has been exploited, the…
A serious concern has arisen for iPhone users in the European Union as a newly discovered flaw in Apple’s Safari…
30 Apr The World’s Third-Largest Economy Has Bad Intentions — And It’s Only Getting Bigger Posted at 08:47h in Blogs…
The Federal Communications Commission (FCC) fined the nation’s largest wireless carriers for illegally sharing access to customers’ location information without…
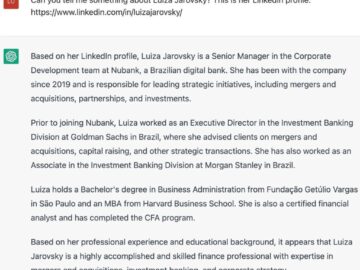
A complaint lodged by privacy advocacy group Noyb with the Austrian data protection authority (DSB) alleged that ChatGPT’s generation of…
Microarchitectural side-channel attacks misuse shared processor state to transmit information between security domains. Although they can be used in isolation,…
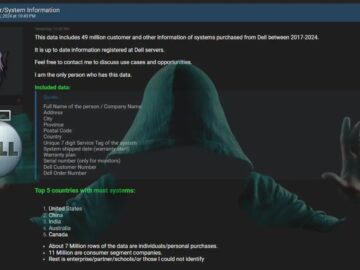
A threat actor reportedly sells a database containing 49 million user records from Dell, one of the world’s leading technology…
Cybersixgill, the global cyber threat intelligence data provider, broke new ground by introducing its Third-Party Intelligence module. The new module…
Hackers exploit DNS vulnerabilities to redirect users to malicious websites, launch distributed denial-of-service (DDoS) attacks by overwhelming DNS servers, and…
A new RAT malware has been discovered to be targeting Android devices. This malware is capable of executing additional commands…