Author: Cybernoz
A critical vulnerability in the WP Datepicker WordPress plugin was identified, affecting over 10,000 active installations. This Arbitrary Options Update…
KnowBe4, the provider of the world’s largest security awareness training and simulated phishing platform, today announced it has entered into…
Hackers exploiting a critical Windows flaw (CVE-2022-38028) in the Print Spooler service. Patch immediately to block APT28 (Forest Blizzard and…
Analysts from Silent Push, a data analytics firm, have uncovered several UK government websites sending user data to a controversial…
Citizen Lab investigated the security of cloud-based pinyin keyboard apps and found that eight out of nine vendors transmitted user…
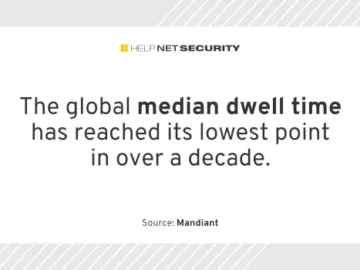
While the use of zero-day exploits is on the rise, Mandiant’s M-Trends 2024 report reveals a significant improvement in global…
SAP has reported revenue of €7bn for the first quarter of 2024, an increase of 8%. It posted an increase…
New Relic announced New Relic AI monitoring with a suite of new features to meet the evolving needs of organizations…
Software problems at ITV News have led to “very narrow escapes” after technology failures came close to leaving gaps in…
“At this time, there is no contract and there is no plan to move forward with the company,” a spokesperson…
Binarly releases the Binarly Transparency Platform v2.0 with features for continuous post-build compliance, visibility into the security posture of IoT…
Apr 24, 2024NewsroomEncryption / Mobile Security Security vulnerabilities uncovered in cloud-based pinyin keyboard apps could be exploited to reveal users’…