Author: Cybernoz
GISEC Global is taking place from April 23 to April 25, 2024, at the Dubai World Trade Centre. Here are…
Researchers identified a cyberattack by the Sandworm group targeting critical infrastructure in Ukraine in March 2024. The attack aimed to…
IBM is reportedly close to finalizing negotiations to acquire HashiCorp, a prominent cloud infrastructure software market player. This potential acquisition…
Sometimes the best advice is free advice. Especially in cybersecurity, where understanding the ‘why’ behind attacks can be as crucial…
The street lights in Leicester City cannot be turned off due to a cyber attack Pierluigi Paganini April 24, 2024…
Hackers primarily use ransomware to gain financial gain from their victims by blackmailing them for payments to recover their encrypted…
A new malware campaign has been exploiting the updating mechanism of the eScan antivirus software to distribute backdoors and cryptocurrency…
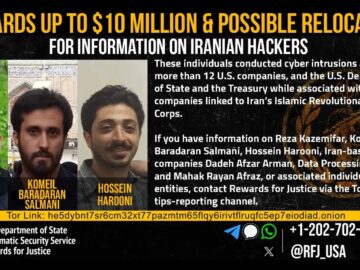
US offers a $10 million reward for information on four Iranian nationals Pierluigi Paganini April 24, 2024 The Treasury Department’s Office…
A new type of malware dubbed “Wavestealer” has been identified. This malicious software reportedly steals sensitive information such as login…
The United States Justice Department has announced big rewards for information leading to the capture of four Iranian nationals. These…
Alert fatigue represents more than a mere inconvenience for Security Operations Centre (SOC) teams; it poses a tangible threat to…
Change Healthcare, a subsidiary of UnitedHealth Group, has confirmed the transfer of 350 bitcoins, equivalent to $22 million USD, to…