Author: Cybernoz
The ability of the United States to intercept and store Americans’ text messages, calls, and emails in pursuit of foreign…
The transport and logistics (T&L) industry is a crucial player in today’s interconnected world, enabling the seamless movement of goods…
BleepingComputer recently reported how a GitHub flaw, or possibly a design decision, is being abused by threat actors to distribute malware using…
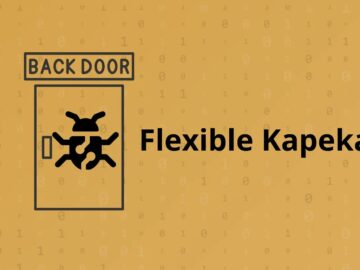
A new backdoor named “Kapeka” has been identified to be attacking victims in Eastern Europe since mid-2022. Kapeka is a…
Organised by Eskenzi PR in media partnership with the IT Security Guru, the Most Inspiring Women in Cyber Awards aim to shed light…
A significant vulnerability has been identified in Citrix’s monitoring tool, uberAgent. If exploited, this flaw could allow attackers to escalate…
In 2024, a significant shift in corporate response to ransomware attacks has emerged, reflecting a resolute stance against capitulation to…
This week on the Lock and Code podcast… Our Lock and Code host, David Ruiz, has a bit of an…
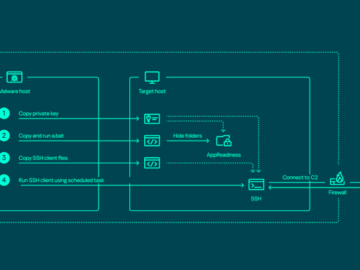
Apr 22, 2024NewsroomNetwork Security / Endpoint Security The threat actor known as ToddyCat has been observed using a wide range…
Synlab Italia has suspended all its medical diagnostic and testing services after a ransomware attack forced its IT systems to…
Advanced Persistent Threat (APT) group known as ToddyCat, new insights have emerged regarding their sophisticated methods of hijacking network infrastructure to steal sensitive data from governmental organizations across the Asia-Pacific region. This…
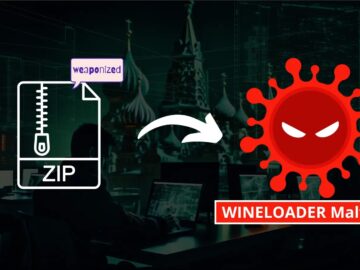
APT29, a Russian threat group, targeted German political parties with a new backdoor called WINELOADER using spear-phishing emails containing malicious…