Author: Cybernoz
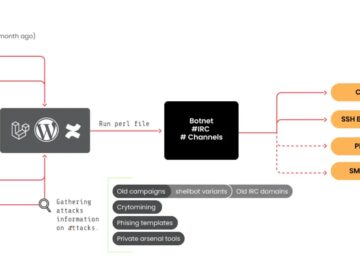
The cybersecurity community is again on high alert as the notorious botnet group RUBYCARP, known for its SSH brute force…
Apr 10, 2024The Hacker NewsWebinar / Identity Security We all know passwords and firewalls are important, but what about the…
Multiple vulnerabilities have been discovered in FortiOS and FortiProxy that were related to administrator cookie leakage, arbitrary command execution and…
A new critical vulnerability has been discovered in two of the Rust standard libraries, which could allow a threat actor…
The UK needs to build on its relationship with South Korea to improve its semiconductor supply chain resiliency. This is among…
Cybersecurity in the Evolving Threat Landscape Pierluigi Paganini April 10, 2024 As technology evolves and our dependence on digital systems…
Greylock Mckinnon Associates Data Breach Exposes Sensitive Information of 340,000 Individuals A significant cybersecurity incident has affected a defense contractor…
Two new techniques uncovered in SharePoint enable malicious actors to bypass traditional security measures and exfiltrate sensitive data without triggering…
In the ever-evolving landscape of cybersecurity, two critical components stand out: data security management and cloud security management. As businesses…
Next week, Diverto is set to release a comprehensive report on Croatia’s cybersecurity landscape. This report will provide a detailed…
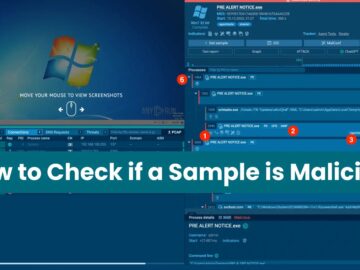
ANY.RUN’s Process Tree shows all the processes that start when a file or URL is run in its sandbox, along…
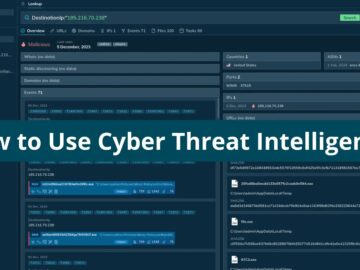
Cyber Threat Intelligence (CTI) is a process that actively gathers and analyzes information on potential cyber threats, including Indicators of…