Author: Cybernoz
[By Mike Walters, President and co-founder of Action1] In 2023, we witnessed numerous security vulnerabilities making headlines, with a few…
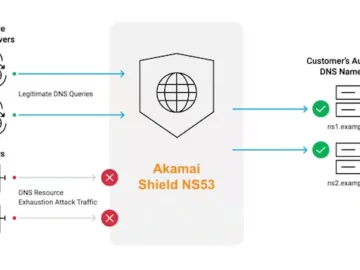
Akamai launched Akamai Shield NS53, a product that protects on-premises (on-prem) Domain Name System (DNS) infrastructure from resource exhaustion attacks….
2023 CL0P Growth Emerging in early 2019, CL0P was first introduced as a more advanced version of its predecessor the…
Top executives of Sirena-Travel JSC, the developer behind the Leonardo airline ticket reservation system, find themselves at the center of…
While the UK’s cyber security skills gap is no secret, it seems there has been little progress made in solving…
Targus International, LLC and its affiliates fell victim to a sophisticated cyberattack. The company, an indirect subsidiary of B. Riley…
New (down)loader malware called Latrodectus is being leveraged by initial access brokers and it looks like it might have been…
Sometimes the consequences of a stolen identity exceed anything you could have imagined. Matthew David Keirans, a 58-year-old former hospital…
Police forces are checking intelligence and criminal databases following warnings of errors in data supplied to police and intelligence services…
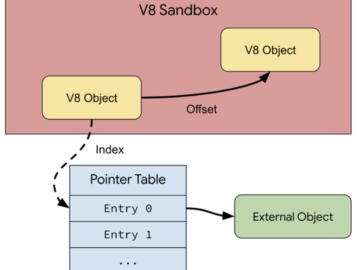
Google announces V8 Sandbox to protect Chrome users Pierluigi Paganini April 09, 2024 Google announced support for a V8 Sandbox in the…
Threat actors have been discovered exploiting a Fortinet Forticlient EMS vulnerability to install unauthorized RMM tools and PowerShell backdoors on…
In a recent announcement, the team behind the widely acclaimed source code editor, Notepad++, has issued a call to arms…