Author: Cybernoz
LastPass Evolves Secure Access Experiences to Combat Shadow IT and AI Risks for CISOs Picture your organization humming along, with…
When you are done with the burner phone, make sure that you get rid of it in a thoughtful way…
Seraphic today announced at Fal.Con 2025 that its Secure Enterprise Browser (SEB) solution is now available for purchase in the…
Clients should have clear expectations of a cloud SLA, and if a provider falls short, they must be held accountable….
The web browser has quietly become one of the most critical components of enterprise infrastructure—and one of the most dangerous….
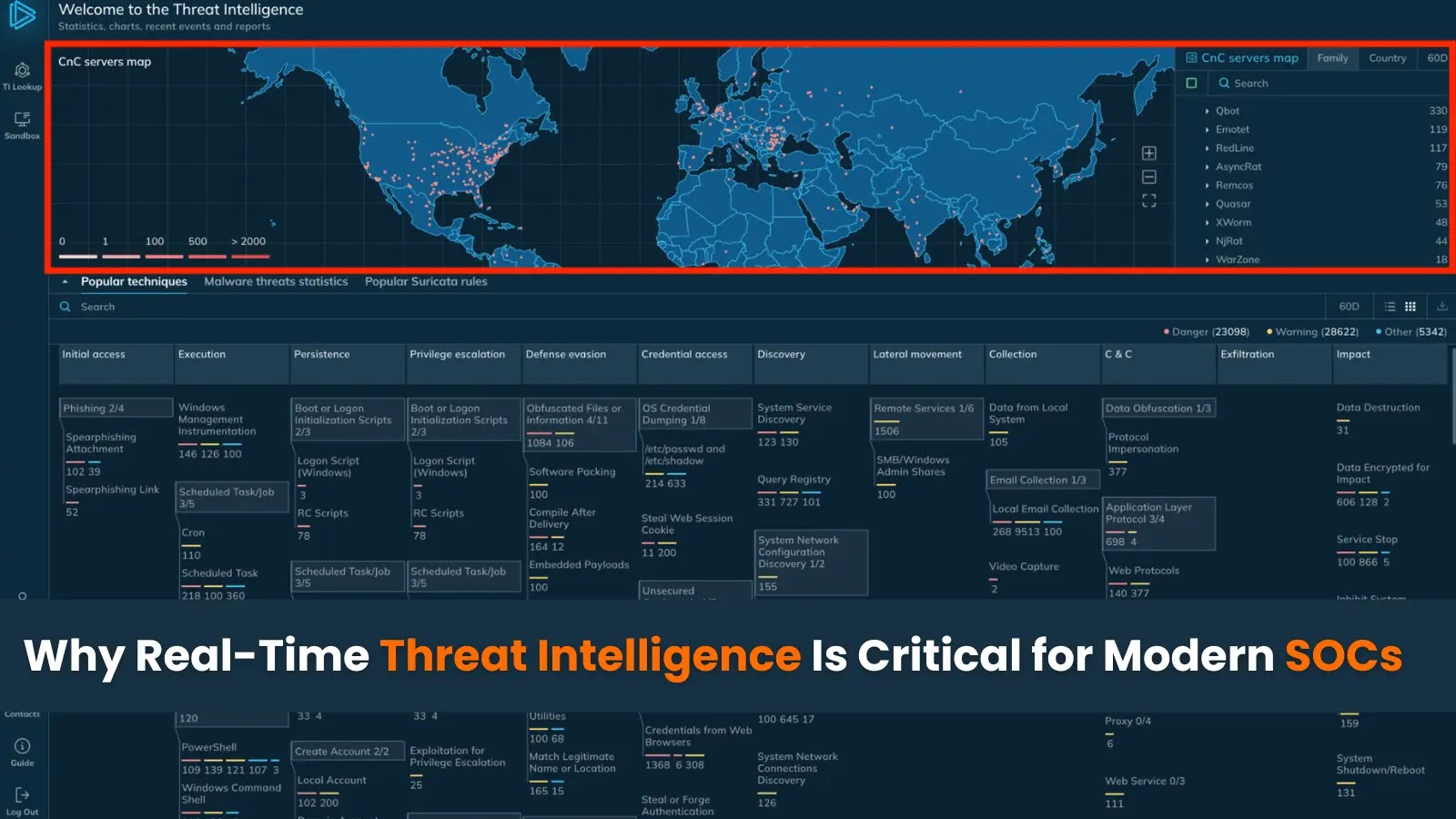
Security Operations Centers (SOCs) exist under ever-increasing pressure to detect and respond to threats before they escalate. Today’s fast-moving adversaries…
Sekoia.io’s Threat Detection and Response (TDR) team has uncovered a sophisticated campaign by APT28 that weaponizes Signal Messenger to deploy…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
When one person on your IT team is VMware certified, that’s a win. But when your entire team is certified?…
RevengeHotels, a financially motivated threat group active since 2015, has escalated its operations against hospitality organizations by integrating large language…
A security vulnerability has been discovered in LG WebOS TV systems that allows attackers to gain complete control over affected…
Sep 16, 2025Ravie LakshmananAd Fraud / Mobile Security A massive ad fraud and click fraud operation dubbed SlopAds ran a…