Author: Cybernoz
A common misconfiguration in popular web servers that support HTTP2 exposes them to low-effort denial-of-service attacks, according to security researcher…
Image: Midjourney Attackers are now actively targeting over 92,000 end-of-life D-Link Network Attached Storage (NAS) devices exposed online and unpatched…
Two key US lawmakers have struck a deal on draft bipartisan data privacy legislation that would restrict consumer data that…
Greylock McKinnon Associates data breach exposed DOJ data of 341650 people Pierluigi Paganini April 08, 2024 Greylock McKinnon Associates, a…
The Significance of Credential Rotations In today’s digital landscape, the significance of regular credential rotations cannot be overstated. Unfortunately, not…
Almost 2,000 hacked WordPress sites now display fake NFT and discount pop-ups to trick visitors into connecting their wallets to…
Coles Group is using generative AI to distil about 40,000 comments from customers each week into a handful of key…
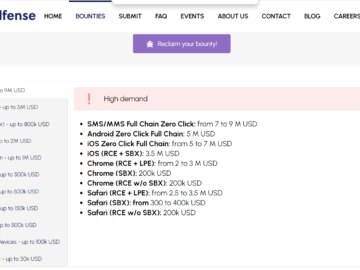
Crowdfense is offering a larger 30M USD exploit acquisition program Pierluigi Paganini April 08, 2024 Zero-day broker firm Crowdfense announced…
Image: Midjourney Google is rolling out an upgraded Find My Device network to Android devices in the United States and…
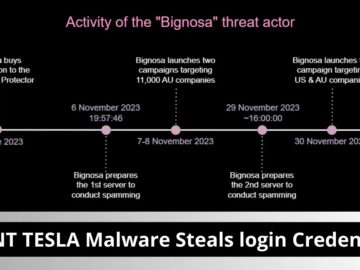
Researchers investigated a recent Agent Tesla malware campaign targeting US and Australian organizations, which used phishing emails with fake purchase…
Operations at UK veterinary services provider CVS Group is being disrupted by a developing cyber incident of a currently-undisclosed nature,…
The Australian Space Agency’s first chief technology officer, Aude Vignelles, has announced that she is to leave her role. Vignelles…