Author: Cybernoz
Cancer treatment and research center City of Hope is warning that a data breach exposed the sensitive information of over…
Security researcher Bartek Nowotarski disclosed a new class of vulnerabilities within the HTTP/2 protocol, known as the HTTP/2 CONTINUATION Flood….
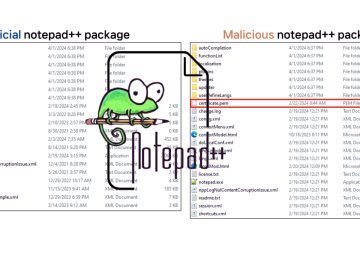
The AhnLab Security Intelligence Center (ASEC) has detected a sophisticated cyberattack targeting users of the popular text and code editor,…
In recent times, cyber attacks have targeted various facets of our digital infrastructure, ranging from national networks to IoT devices….
On April 2, 2024, Jackson County tweeted that it had identified significant disruptions within its IT systems, “potentially attributable to…
A suspected Vietnamese-origin threat actor has been observed targeting victims in several Asian and Southeast Asian countries with malware designed…
Extensive automation of cyber security operations could become a game-changer, and the concept of playbook-driven security automation is advancing rapidly. …
Diving into pentest readiness, this comprehensive preparation guide is adaptable to different types of pentest, regardless of the target’s size…
Among the never-ending list of malicious software that threat actors use in cyber attacks are viruses, worms, trojans, ransomware, spyware,…
Google fixed three vulnerabilities in the Chrome browser on Tuesday, along with another zero-day exploit that was exploited during the Pwn2Own Vancouver…
AT&T, a leading American telecommunications company, is facing a wave of lawsuits following a data breach that exposed the sensitive…
Image source: Pixabay It seems each week brings news of another attack – millions drained from DeFi protocols, NFTs swiped,…