Author: Cybernoz
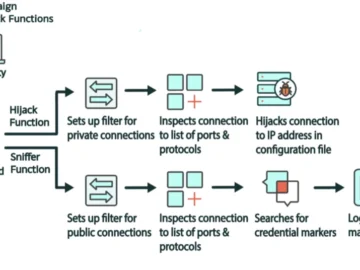
Cuttlefish, a new malware family that targets enterprise-grade small office/home office (SOHO) routers, is used by criminals to steal account…
May 02, 2024NewsroomCyber Attack / Data Breach Cloud storage services provider Dropbox on Wednesday disclosed that Dropbox Sign (formerly HelloSign)…
Barnsley has become one of the first councils to roll out generative AI (GenAI) tools across its entire organisation as…
Cloud storage and file sharing company Dropbox disclosed a security breach that resulted in an unauthorized access to sensitive information,…
CISA adds GitLab flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini May 02, 2024 CISA adds GitLab Community and Enterprise Editions…
On this World Password Day, we should all pause and think about how we can adopt passkeys. Passkeys represent a significant…
Russian hacktivists increasingly target small-scale operational technology (OT) systems across North America and Europe. These attacks, primarily focused on the…
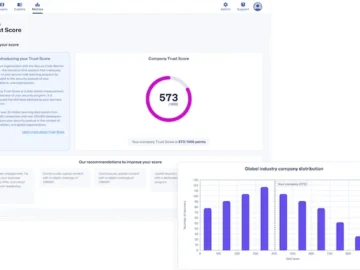
Secure Code Warrior unveiled SCW Trust Score, a benchmark that quantifies the security posture of organizations’ developer teams. SCW Trust…
Like antivirus software, vulnerability scans rely on a database of known weaknesses. That’s why websites like VirusTotal exist, to give…
Nestled in the sun-kissed hills of Provence, just north of Cannes and Antibes, is Sophia Antipolis, a renowned technology and…
Over a million Australians who frequented pubs and clubs have likely had their critical information exposed in Outabox data breach,…
A new variant of the notorious Adload malware has been discovered to bypass the latest updates to Apple’s built-in antivirus,…